5 Cryptography Courses to Secure Sensitive Data for Security Engineers
Are you a security engineer who wants to upgrade your skills to combat the increasing threat of cyber attacks? If yes, then you have landed on the right page. In this piece, we will not only explore how you can do it using cryptography but will also explore the top five online cryptography courses to secure sensitive data.
Each of these cryptography courses listed below offers a unique perspective on securing data. So, why wait? Let's begin!
Table of Content (TOC)
- What is Cryptography?
- How Cryptography Can Help Secure Sensitive Data?
- 5 Best Online Cryptography Courses
What is Cryptography?
Cryptography is a technique of securing data by converting it from plain text into encoded format, known as cypher text. Doing so ensures that only an authorized individual is able to view or alter the data.
Cryptography involves multiple protocols and algorithms to achieve key objectives like - integrity, authentication, confidentiality, and non-repudiation of data. Intrested in learning more about cryptography? If yes, read the different types of cryptography article.
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
How Cryptography Can Help Secure Sensitive Data?
Cryptography secures sensitive data by transforming or converting it into a format that's unreadable by an unauthorized user. To achieve this, these techniques are used:
- Encryption: Converts plain text into ciphertext using algorithms and keys. Even if the data is intercepted, it remains incomprehensible without the proper decryption key.
- Authentication: Verifies the identity of users and devices to make sure that only authorized individuals or parties can access the data.
- Integrity: Ensures that data has not been altered during transmission. Techniques like hashing generate a unique value for the data, which changes if the data is tampered with.
- Non-repudiation: Prevents the sender from denying they sent a message, providing proof of the origin and integrity of the data.


5 Best Online Cryptography Courses
These five courses have been carefully selected after comparing them against 100+ online cryptography courses and evaluating them on various parameters such as - vendor, price, knowledge gain, etc. Here are the key highlights of these five courses:
| Course | Fees (INR) | Instructor | Provider |
| Penetration Testing, Threat Hunting, and Cryptography | Depends on time taken to finish the course.
|
Dr. Manish Kumar, Dee Dee Collette, and IBM Skills Network Team | Coursera |
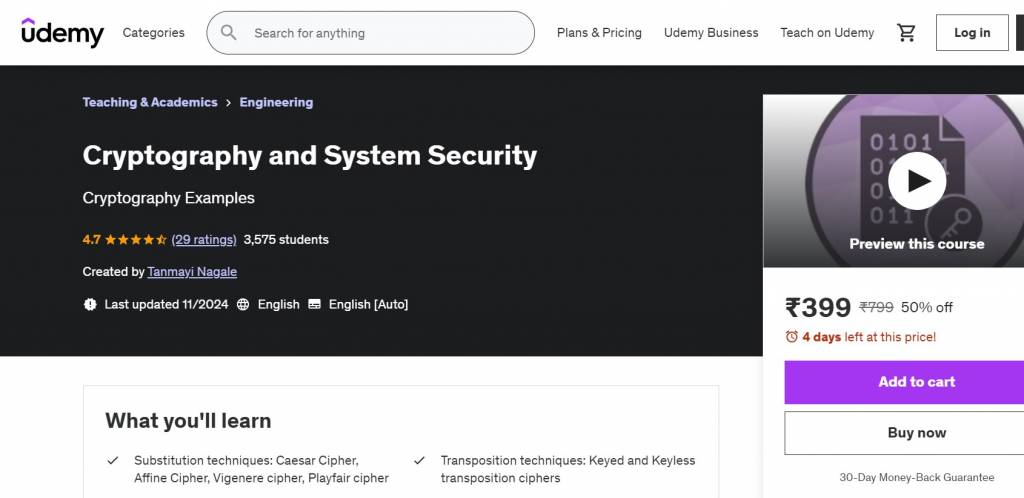
| Cryptography and System Security | 799 | Tanmayi Nagale | Udemy |
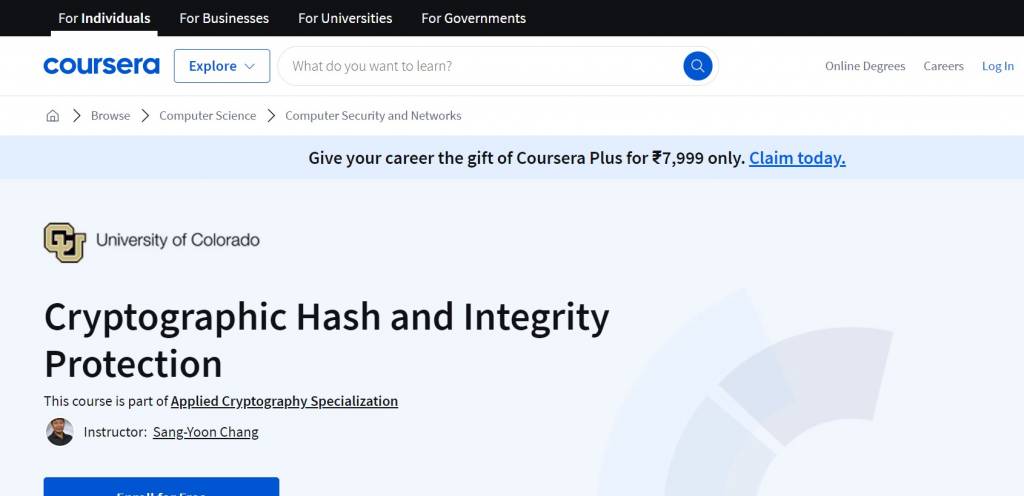
| Cryptographic Hash and Integrity Protection | Depends on time taken to finish the course.
|
Sang-Yoon Chang | Coursera |
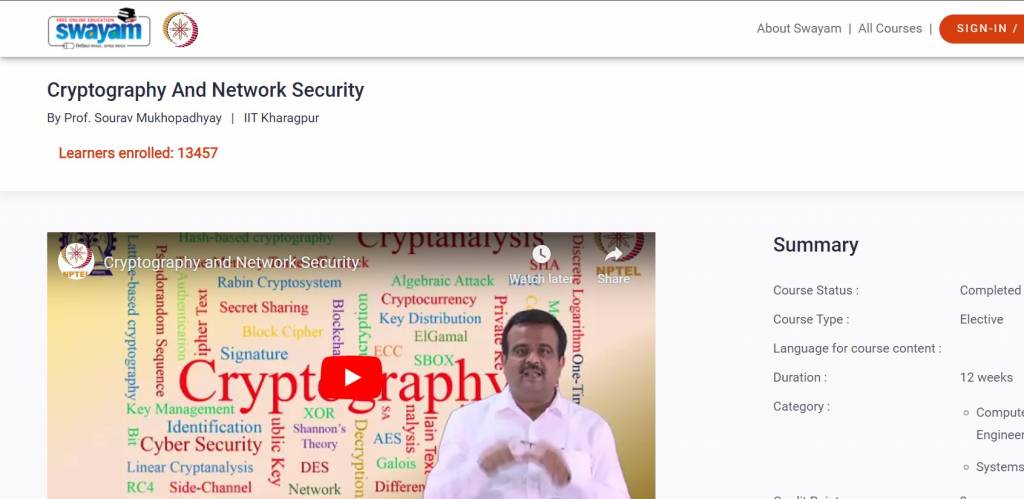
| Cryptography And Network Security | Free | Prof. Sourav Mukhopadhyay | Swayam |
| Security Engineer |
|
Dev Badlu, Rod Soto, Abhinav Singh, and Taylor Lobb |
Penetration Testing, Threat Hunting, and Cryptography
This IBM course on Coursera covers topics such as encryption, decryption, hashing techniques, common cryptographic attacks and cryptanalysis methods. Apart from that, the course also teaches you how to create pen testing reports, perform threat hunting, etc., and provide hands-on labs and projects.
To pursue this course, it is recommended that you have fundamental knowledge of IT systems and cybersecurity principles before starting it. To date, 90078+ students have already enrolled in this course, and it has been rated 4.6 out of 5.
Cryptography and System Security
This Udemy course will teach you about security goals and concepts in-depth, focusing on confidentiality, availability, integrity, and related principles like non-repudiation and authentication. You will also learn about hashing algorithms, network vulnerabilities, security protocols, and digital signature schemes to ensure secure data transmission.
To pursue this course, it is recommended that you have a fundamental knowledge of mathematics before starting it. To date, 3600+ students have already enrolled in this course, and it has received a 4.7 instructor rating out of 5.
Cryptographic Hash and Integrity Protection
This University of Colorado course on Coursera is a part of the Applied Cryptography specialization. It covers various topics such as cryptographic hash functions, their use in the hash chain and hash tree (Merkle tree), message authentication, digital signature, two MAC implementations in Data Authentication Algorithm (DAA) and Cipher-Based MAC (CMAC), etc.
The duration of the course is 8 hours (3 weeks at 2 hours per week). To date, 8887+ students have already enrolled in this course, and it has received a 4.5 rating out of 5.
Cryptography And Network Security
This IIT Khragpur course on Swayam introduces you to the cryptography and cryptanalysis concepts. The course provides a basic understanding of previous attacks on cryptosystems to prevent future attacks. The course also covers some advanced topics like identity-based encryption, functional encryption, attribute-based encryption, two-party/multi-party computation, bitcoin and cryptocurrency and postquantum cryptography. The course aims to help you understand the challenges of cybersecurity, which include network, data, mobile, endpoint, and cloud security.
The duration of the course is 12 weeks, and it is free to enrol. But if you want a certification, you must register and write the proctored exam in person at any designated exam centres. The exam is optional and costs a fee of INR 1000. To date, 13457+ students have already enrolled in this course.
Security Engineer
This Udacity course teaches you how to protect a company's computer systems, networks, applications and infrastructure. During the course, you will learn about various important topics, such as data encryption, vulnerability assessment, hashing, public key certificates, vulnerability scanning and patching, server hardening strategy, etc.
The duration of the course is 4 months, and it has received a 4.7 rating out of 5. To pursue this course, it is recommended that you know Linux (basic), computer networking basics, Windows operating system and scripting.





Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio