What is an Active Attack?
Imagine you receive an email from your bank asking you to verify your account details. Everything looks normal—the logo, the language, even the sender’s address. You click the link and enter your credentials. Within minutes, your account is hacked. This is an example of an active attack, where hackers manipulate data to gain control.
Cybercriminals don’t just steal information; they intercept, alter, and disrupt systems. From online banking fraud to website defacement, active attacks can cause severe damage. Unlike passive attacks, where data is only monitored, active attacks involve direct interference.
But how do these attacks work? What methods do hackers use? Most importantly, how can you protect yourself? Let’s explore everything you need to know about active attacks in this piece.
Table of Content (TOC)
- What is an Active Attack?
- How Do Active Attacks Work?
- Types of Active Attacks
- Real-Life Examples of Active Attack
- How to Detect and Respond to Active Attacks?
- How to Prevent an Active Attack?
- What is the Difference Between Active and Passive Attacks?
What is an Active Attack?
An active attack is a type of cyberattack where an attacker actively interferes with a system or network. Unlike passive attacks, which focus on stealing information silently, active attacks involve modifying, disrupting, or damaging data and services. The goal is to gain unauthorized access, alter sensitive information, or make systems unusable.
These attacks can take many forms, such as hacking, data manipulation, denial-of-service (DoS), and session hijacking. Since active attacks involve direct interaction with the target system, they are often easier to detect but can cause immediate and severe damage if not prevented.
To understand cybersecurity in depth, including certifications, course fees, syllabus, top colleges, and career opportunities, check out our detailed guide on Cyber Security: Certifications, Course Fees, Syllabus, Top Colleges, Salary, etc.
How Do Active Attacks Work?
Active attacks follow a structured process, from gathering information to executing and maintaining unauthorized access. Below are the key steps involved:
- Reconnaissance: In this step, the attacker gathers information about the target, such as system vulnerabilities, IP addresses, or employee details.
- Gaining Access: In this step, the attacker uses cyberattack techniques like phishing, social engineering, malware injection, etc., to pass the system's or network's security and enter.
- Execution: In this, the attacker launches the attack to either modify the data, inject malware, or hijack a session.
- Maintaining Access: In this fifth step, the attacker installs backdoors or rootkits to stay undetected in the system.
- Covering Tracks: In this last step, the attacker deletes or alters the logs to erase any traces of the attack and avoid detection.
Tools Used in Active Attacks
| Tool | Purpose |
|---|---|
| Metasploit | Penetration testing and exploiting vulnerabilities. |
| Wireshark | Packet sniffing to capture and analyze network traffic. |
| Nmap (Network Mapper) | Scanning and discovering open ports and network devices. |
| Aircrack-ng | Cracking Wi-Fi passwords and monitoring wireless networks. |
| Burp Suite | Web security testing and intercepting HTTP requests. |
| Mimikatz | Extracting passwords from Windows systems. |
| BeEF (Browser Exploitation Framework) | Exploits browser vulnerabilities to launch attacks. |
Interested in knowing which are the top 10 tools that are used in Penetration testing? If yes, read the Top 10 Penetration Testing Tools of 2025 article.
Types of Active Attacks
Here are some of the main types of active attacks:
| Type of Attack | Description | Example |
|---|---|---|
| Masquerade Attack | The attacker pretends to be a legitimate user to gain access. | A hacker using stolen credentials to log into a system. |
| Replay Attack | The attacker captures and reuses a valid data transmission. | Reusing an old login request to access a secure system. |
| Session Hijacking | The attacker takes over an active session between a user and a system. | Taking control of a user’s banking session to transfer money. |
| Man-in-the-Middle (MitM) Attack | The attacker intercepts communication between two parties to steal or alter data. | A hacker intercepting online banking transactions to steal credentials. |
| Denial-of-Service (DoS) Attack | The attacker floods a network or website with traffic, making it unavailable. | Overloading a website with fake traffic to crash it. |
| Spoofing Attack | The attacker disguises as a trusted entity to trick users or systems. | A fake email appearing to be from a bank asking for login details. |
| Ransomware Attack | Malicious software encrypts files and demands payment for their release. | A company’s files are locked until a ransom is paid to the hacker. |
| SQL Injection Attack | The attacker inserts malicious SQL code to manipulate databases. | Gaining unauthorized access to user information from a website. |
| Advanced Persistent Threat (APT) | A long-term attack where hackers secretly infiltrate a system to steal data. | Cybercriminals gaining silent access to a government network for months. |

Real-Life Examples of Active Attack
Here are some of the notable active attacks in the last few years:
- Yahoo Data Breach (2013–2014): Hackers stole data from 3 billion user accounts, including emails, passwords, and security questions.
- Sony Pictures Hack (2014): Attackers used malware to wipe data, leak sensitive emails, and disrupt operations.
- Equifax Data Breach (2017): Exploited a software vulnerability to steal the personal data of 147 million people.
- WannaCry Ransomware Attack (2017): Hackers used the EternalBlue exploit to spread ransomware, locking files in over 200,000 computers worldwide.
- NotPetya Attack (2017): Disguised as ransomware but aimed at data destruction, impacting global companies like Maersk and FedEx.
- Marriott Data Breach (2018): Attackers remained in the system for four years, stealing the personal and financial data of 500 million guests.
- SolarWinds Supply Chain Attack (2020): Hackers compromised software updates, affecting government agencies and major corporations.
- Colonial Pipeline Ransomware Attack (2021): Disrupted fuel supply across the U.S. East Coast by encrypting critical system data.


How to Detect and Respond to Active Attack?
Here are some signs that indicate your system or network may be encountering an active attack:
- Unusual Network Traffic: Monitor for unexpected spikes in data transfer, which may indicate an attack.
- Unauthorized Access Attempts: Track failed login attempts and suspicious logins from unknown locations.
- System Performance Issues: Slow performance, crashes, or unusual errors can signal a cyberattack.
- Unexpected File Modifications: Attackers often alter or delete files to cover their tracks.
- Security Alerts from Tools: Use IDS/IPS (Intrusion Detection/Prevention Systems) to detect suspicious activity.
If you suspect that you are being attacked by a hacker using an active attack, follow these practices:
- Isolate the Affected System: Disconnect compromised devices from the network to prevent further damage.
- Identify the Attack Type: Analyze logs, alerts, and forensic data to determine the nature of the attack.
- Contain the Threat: Block malicious IPs, disable compromised accounts, and patch vulnerabilities.
- Remove the Attacker's Access: Eliminate malware, close security gaps, and revoke unauthorized access.
- Restore from Backups: Recover data from clean backups to ensure business continuity.
- Strengthen Security Measures: Update security policies, enforce multi-factor authentication (MFA), and educate employees.
- Report & Document: Inform cybersecurity authorities, document the incident, and improve future defences.
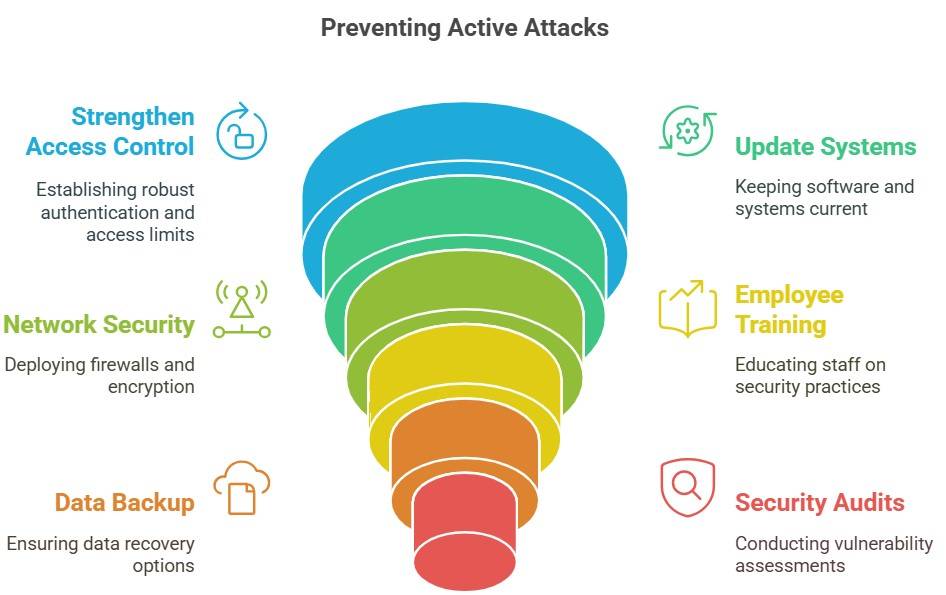
How to Prevent an Active Attack?
- Use Strong Authentication: Enable multi-factor authentication (MFA) and strong passwords.
- Keep Systems Updated: Regularly update software and apply security patches.
- Secure Networks: Use firewalls, IDS/IPS, and encrypt sensitive data.
- Train Employees: Educate staff on phishing, social engineering, and safe browsing.
- Backup Data Regularly: Store encrypted backups offline and test recovery procedures.
- Conduct Security Audits: Perform regular vulnerability assessments and penetration testing.
- Monitor for Threats: Use real-time threat detection and an incident response plan.
What is the Difference Between Active and Passive Attacks?
Let's explore the difefrence between active attack and passive attack in a tabular format, for a better understanding:
| Benchmark | Active Attack | Passive Attack |
|---|---|---|
| Definition | An attack where the attacker modifies, disrupts, or damages a system or data. | An attack where the attacker silently monitors or steals data without making changes. |
| Intent | To alter, damage, or take control of the system. | To gather information secretly without detection. |
| Impact | High – affects system integrity, availability, and confidentiality. | Low – primarily affects confidentiality. |
| Detection | Easier to detect due to noticeable disruptions or modifications. | Harder to detect as it doesn’t alter data or systems. |
| Examples | Man-in-the-Middle (MitM), Denial-of-Service (DoS), Ransomware, SQL Injection. | Eavesdropping, Traffic Analysis, Keylogging, Passive Reconnaissance. |
| Defense Methods | Firewalls, Intrusion Detection Systems (IDS), Strong Authentication, Encryption. | Encryption, Secure Communication Channels, Network Monitoring. |
In case, you want to learn in-depth how active and passive attacks differ, refer to the Difference Between Active and Passive Attacks article.
Conclusion
Active attacks involve direct interference with systems and data, leading to severe consequences. You can protect yourself and your sensitive information by staying informed and using security best practices that were discussed in this piece.
Must Read Articles:





Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio