What Is A Data Breach and How To Prevent It?
A data breach happens due to a cyberattack that enables cyber attackers to gain unauthorized access to a system or network and steal customers’ personal or classified information. Today, it is one of the most severe issues threatening government and commercial sectors.
So what exactly is a data breach? Before understanding and answering this question, let’s go through the topics that we will be covering in this blog:
- What is a data breach?
- What causes a data breach?
- Widespread attacks used by attackers to conduct a data breach
- Real-life examples of a data breach in India
- India’s data breach law
- How to prevent data breaches?
What is a data breach?
A data breach occurs when private or secured information is disclosed to an unauthorized person as a result of a cyberattack. In this attack, the files are viewed or shared without the owner’s permission. Data breaches can occur in organizations or businesses of any size, from small to large.
In today’s world, sensitive and confidential data keeps on moving from one place to another over the Internet. Hence data breaches have become a significant security concern. Because of this continuous transfer of information, attackers can attempt data breaches on almost every individual or corporation they choose.
You can also explore – What is cybersecurity?
A data breach can be either deliberate or accidental. An attacker may attack an organization gaining access to their database. Put another way, an employee at that same company may unintentionally publish the data on the Internet. In either case, criminals can gain access to sensitive data and make a considerable profit by selling it on the dark web.
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
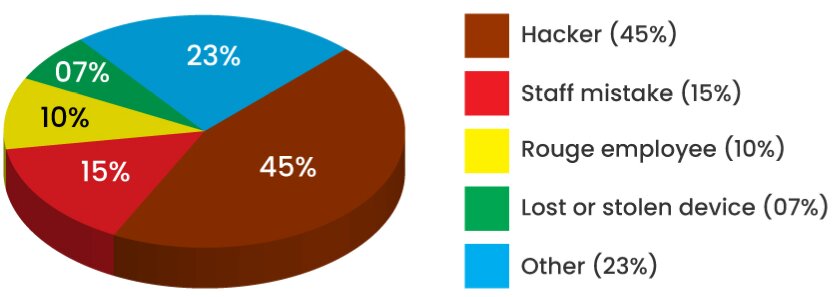
What causes a data breach?
Many reasons can result in a data breach. But a few of the most popular ones are:
Hacker: Hackers are one of the most common causes of data breaches. These hackers target specific people or organizations in order to obtain sensitive information. They employ a variety of techniques to gain unauthorized access in order to steal user login credentials, financial information, sensitive or confidential information, and so on.
Staff mistake: Data breaches can result from human error or carelessness. An example would be employee reading files on a coworker’s computer without the proper authorization permissions. Because an unauthorized person reads the data, it is considered a data breach.
Rouge employee: A rouge employee can be someone who has access to protected information and intentionally exposes it, often for personal gain. A high-level government employee selling secrets to foreign governments is one example.
Lost or stolen devices: If a lost computer or smartphone containing confidential information falls into the wrong hands, it can result in a data breach.
Other: There are various other reasons that can result in a data breach, such as lack of encryption or misconfigured web app or server, etc.
Widespread attacks used by attackers to conduct a data breach
There are various attacks that an attacker may use to conduct a data breach. But, some of the most common or popular attacks are:
Phishing: It is a social engineering attack in which a hacker pretends to be a trustable entity in order to trick a person into clicking a malicious link, which results in malware setup or the disclosure of confidential information.
Trojan Horse: A Trojan Horse is a malicious program that appears to do one thing but actually does something else. Hackers can conceal Trojans as free software, videos, music, etc.
Distributed-Denial-of-Service: A DDoS attack is a malicious attempt to make an online service inaccessible to users, generally by temporarily interrupting or dismissing the services of the hosting server.
Social engineering: In this, an attacker manipulates their target to gain unauthorized access to systems.
Logic Bombs: A logic bomb is a sequence of malicious code that is purposefully implanted into a program in order to cause harm to a system or a network when certain factors are met.
Brute Force: In this attack, an attacker repeatedly tries different password and user name variations until it gains access in order to steal confidential information.
Real-life examples of a data breach in India
Indian Computer Emergency Response Team reported over 962.7 million cybersecurity incidents in 2021. CERT is in charge of monitoring and responding to cybersecurity threats. Here are a few of the most famous cases:
- Domino’s Pizza was the most recent victim of a data breach attack. In 2021, the organization reported that data from 18 crore orders, including order details, email addresses, phone numbers, and credit card information, had been leaked on the dark web.
- Upstox, an Indian trading platform, has openly admitted to a breach of know-your-customer (KYC) data. The government later found that attackers were using the exact data for committing identity theft.
- A cyberattack on airline data service provider SITA’s systems resulted in passengers’ personal information leaks. Personal data of 4.5 million Air India passengers worldwide is still available on the dark web, containing confidential information such as credit card numbers, phone numbers, email addresses, and so on.
India’s data breach law
- Section 72A of the IT Act provides for up to three (3) years in prison if personal information is disclosed in violation of a lawful contract or without consent.
- Section 70B(7) of the IT Act, read in conjunction with the CERT-In Directions, provides up to one (1) year in prison for failing to provide information to CERT-In and to comply with CERT-reporting In’s requirements.
How to prevent data breaches?
This problem does not have a single solution. The most practical methods for preventing data breaches include standard security practices such as:
- Only provide your Aadhar number and other confidential information when necessary.
- Educate your employees on the best security practices for your company.
- Make strong passwords from uppercase and lowercase letters, numbers, and special character symbols.
- Conduct regular vulnerability assessments.
- Use different passwords for each account. If one of your account passwords is exposed or compromised, this can help to mitigate the damage.
- Update your systems with the most recent operating and application versions to improve security.
- To encourage better user cybersecurity practices, enforce strong credentials and multi-factor authentication.
You can also explore – What is Safe Browsing & How to Turn It On?
Conclusion
You probably have little control over what happens to your data in the event of a data breach. So, rather than being sorry later, take precautions to protect your data now.
FAQs
What are the three most common reasons for data breaches?
Weak and stolen credentials, application vulnerabilities, and malware are the three most common causes of data breaches.
What are the three kinds of data breaches?
Physical, electronic, and skimming data breaches are the three types.
What is the first thing you should do if there is a data breach?
You should immediately initiate an alert and change the login credentials when a breach occurs.
How can security breaches be avoided?
Firewalls, anti-virus, and anti-spyware software are critical tools for protecting your company from data breaches. Set these up correctly by working closely with an internet security team or provider.
How many data breaches occur each day?
According to a report, approximately 20 breaches happen daily worldwide.
How can businesses avoid security breaches?
Limiting access to your most valuable data, conducting employee security awareness training, regularly updating software, developing a cyber breach response plan, and other measures can help prevent cyber security breaches at your company.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio