What is a Dictionary Attack?
In today's time, where most of our personal and professional lives are digitized, securing our online accounts with strong passwords has become more critical. Unfortunately, not all of us take this seriously (59% of users, as per a Google study), and we often use weak and easily guessable passwords that attackers can easily crack using password cracking techniques like dictionary attacks.
In this article, we will explore what a dictionary attack is, how it works, and how you can prevent it from compromising your online security. So, let's get started!
Table of Content (TOC)
- What is a Dictionary Attack?
- How Does Dictionary Attack Work?
-
What are the Consequences of a Successful Dictionary Attack?
- What is the Difference Between Brute Force and Dictionary Attack?
- How to Prevent Dictionary Attacks?
What is a Dictionary Attack?
A dictionary attack is a type of password cracking technique in which attackers try every word in a dictionary or word list as a password to breach password-protected systems. It's like trying every key on a key ring until you find the one that opens the lock. This attack vector is a form of brute force attack.
Attackers use password cracking tools like John the Ripper, Aircrack-ng, Hashcat, and others to make this process more efficient. These tools can rapidly cycle (millions per second) through thousands of dictionary words and their variations and mutations. This is much quicker than manually entering dictionary words as passwords, which can be time-consuming, tedious, and prone to errors.
Note: A word list is a list generated by an attacker that may contain commonly used passwords, phrases, and combinations of letters, numbers, and symbols. It may also be tailored to include industry-specific jargon, slang, and other relevant terms if the target is known to belong to a particular field or interest group.
You should also explore: What is a Salami Attack and How to protect against it?
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
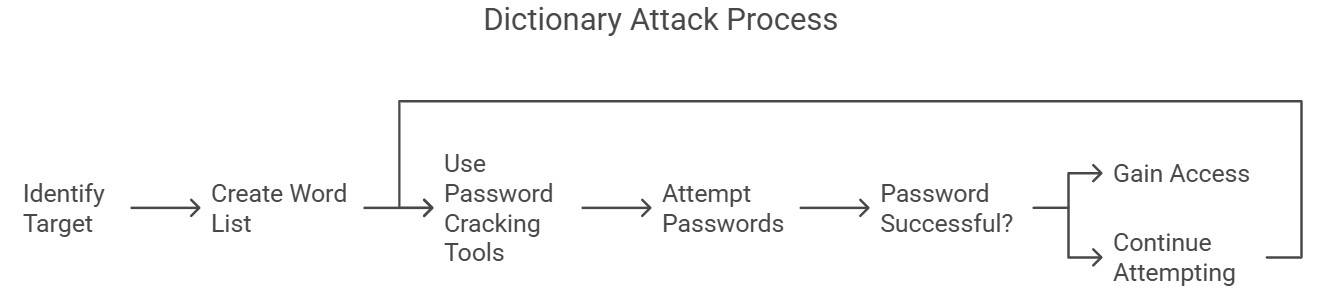
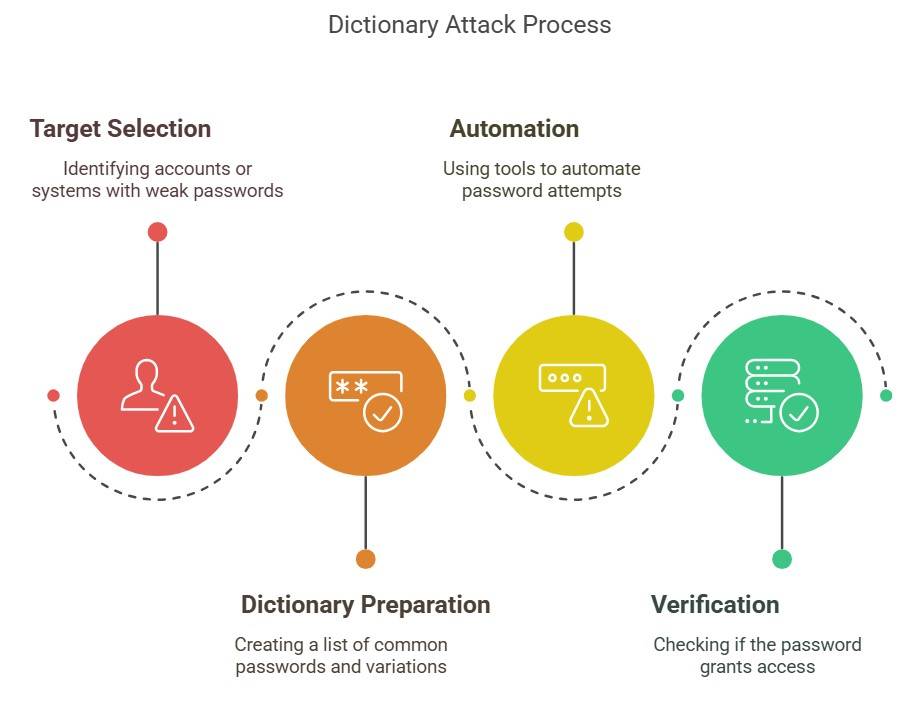
How Does Dictionary Attack Works?
Here's how this attack works:
- Target Selection: The first step is to select the target account, system, or encrypted data with weak password protection or predictable patterns.
- Dictionary Preparation: Once the target is selected, the hacker creates a list of common words, phrases, names and slang, often combined with character substitutions. For example, the dictionary or word list may contain common words such as password, iloveyou, etc., variations like P@ssw0rd, i<3u, etc., usernames with numbers, etc. The attackers may also collect password lists from data breaches and include them in the word list.
- Automation: After the list is generated, hackers use scripts or password-breaking tools to automate the password-guessing process, sequentially trying each entry in the word list.
- Verification: For each guess, the system checks if it grants access or decrypts the data. If successful, the attack is complete.
What are the Consequences of a Successful Dictionary Attack?
A successful dictionary attack can lead to several serious consequences, such as:
- Unauthorized Access: Attackers may gain access to sensitive accounts, such as email, banking, or social media, leading to privacy violations.
- Data Theft: Confidential information, including personal data or corporate secrets, can be stolen and misused.
- Financial Loss: Victims may suffer direct financial losses if attackers access banking accounts or make unauthorized transactions.
- Identity Theft: Personal information can be used to impersonate the victim, resulting in fraud and further financial damage.
- Reputational Damage: For businesses, a successful attack can harm their reputation, leading to loss of customer trust and potential legal consequences.
- Malware Installation: Attackers may install malware to further exploit the compromised system, which can lead to more severe attacks.
- Service Disruption: If critical accounts are breached, services can be disrupted or taken offline, affecting business operations.
- Legal Consequences: Organizations may face legal actions if customer data is compromised, leading to regulatory fines and lawsuits.
What is the Difference Between Brute Force and Dictionary Attack?
The main difference between brute force and dictionary attacks is that in a brute force attack, an attacker tries every possible combination of characters until it finds the correct password. In contrast, an attacker uses a list of potential passwords compiled from dictionaries, common passwords, and known password patterns in a dictionary attack.
To understand the difference between these two types of attacks, let's go through an example in which you need to open a treasure chest that is secured with a combination lock. The lock requires a 4-character password. Each character can be any letter from A to Z (assuming no numbers or symbols for simplicity).
Brute Force Attack Example
Imagine trying to open the lock without any hints about the password. You decide to try every possible combination until you find the right one.
- Method: Start with "AAAA" and continue sequentially: "AAAB", "AAAC", ..., "ZZZZ".
- Effort: You will attempt all 456,976 combinations (26^4 for four letters).
- Time: It takes a significant amount of time as you check every possible combination without skipping any.
- Outcome: You will eventually open the lock, but it might take a long time.
Dictionary Attack Example
Suppose you know that the lock owner tends to use simple, common words or known codes as passwords.
- Method: You have a list of common 4-letter words or known popular codes (e.g., LOVE", CODE, GOLD, LOCK, etc).
- Effort: You try each word on your list. Let's say your list has 100 words.
- Time: Much less time is needed than the brute force method since you only try a limited number of likely combinations.
- Outcome: If the chest owner used a common word or code, you would likely open the lock quickly. But, your attempt would fail if they used a unique or complex password.
How to Prevent Dictionary Attacks?
Here are key steps you can take:
- Utilize Strong Passwords: Ditch weak, easily guessable passwords like "password123" or your pet's name. Instead, use unique passwords that are:
-
-
- At least 12 characters long.
- Contains a mix of uppercase and lowercase letters, numbers, and symbols.
- Avoid personal information like birthdays, anniversaries, or names.
- Refrain from using the same password across different accounts.
-
- Use Passphrases: Instead of simple and common passwords like "hello," use a longer string of words that are memorable and difficult to guess, like "PurpleSkyFlyingHigh1984!" Using passphrases instead of passwords is advantageous as it has:
-
- Length Advantage: Passphrases can be much longer than passwords, significantly increasing the number of possible combinations and making them harder to crack.
- Memorability: They are often easier to remember than complex passwords, as they use phrases that have personal meaning.
- Dictionary Resistance: Since they deviate from shared word lists, they are less susceptible to dictionary attacks.
-
- Utilize a Password Manager: Leverage a password manager to store and manage them securely. It can generate, store, and auto-fill passwords for all your accounts, eliminating the need to remember them yourself.
- Implement Multi-Factor Authentication (MFA): Add an extra layer of security with MFA. Even if a dictionary attack cracks your passphrase, it won't grant access without the additional verification step, like a code sent to your phone.
- Stay Vigilant Against Phishing: Be cautious of suspicious emails, texts, or links. Don't reveal your passphrases or click on unknown links, even if they appear legitimate.
- Keep Software and Devices Updated: Regularly update your operating systems, applications, and devices with the latest security patches. This helps close vulnerabilities that attackers could exploit.
- Be Proactive: Change your passwords or passphrases regularly, even if you haven't experienced any security incidents. Remember, prevention is better than cure!
FAQs
What is a dictionary attack?
A dictionary attack is a method used to break passwords. It uses a list of common words and phrases to guess the password. This method is faster than trying random combinations.
How does a dictionary attack work?
The attacker uses software that tries each word from a predefined list. If the password is in that list, the attacker gains access. This method relies on weak passwords that are often simple words.
Who is at risk of a dictionary attack?
Anyone using weak passwords is at risk. It includes individuals and organizations. Common passwords like "password" or "123456" are easy targets. Strong, complex passwords can help reduce this risk.
How does adding a delay between login attempts impact Dictionary Attacks?
Introducing a delay significantly slows down attackers, making Dictionary Attacks impractical by increasing the time required to test each password guess.
What role does password length play in defending against Dictionary Attacks?
Longer passwords exponentially increase the number of possible combinations, making Dictionary Attacks far less likely to succeed due to the added complexity.
Can Dictionary Attacks bypass Multi-Factor Authentication (MFA)?
No, MFA provides a critical second layer of security. Even if a Dictionary Attack guesses the password, the additional verification step prevents unauthorized access.
Are passwords derived from personal information secure against Dictionary Attacks?
No, passwords based on personal information are often easier to guess with Dictionary Attacks, especially if the attacker has targeted knowledge.
How does the complexity of a password affect its vulnerability to Dictionary Attacks?
Complex passwords that mix letters, numbers, and symbols are less likely to be included in attackers' word lists, significantly reducing the risk of a successful Dictionary Attack.
How can I protect myself from dictionary attacks?
Use strong passwords that combine letters, numbers, and symbols. Avoid common words and phrases. Additionally, consider using two-factor authentication for extra security.
Can dictionary attacks be automated?
Yes, dictionary attacks can be automated using dictionary attack tools, such as Hashcat, John the Ripper, Hydra, Burp Suite, Medusa, etc. These tools can quickly test thousands of passwords from a list.
What is the difference between a dictionary attack and a brute force attack?
A dictionary attack uses a list of words, while a brute force attack tries every possible combination of characters. Brute force attacks take longer but can eventually crack any password.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio