How to Learn Networking from Scratch – Beginner’s Guide
Our daily lives are intricately woven into a vast information and communication network. Whether browsing this blog on your computer, smartphone, or any internet-enabled device, you're already part of this global network. But have you ever wondered how all these devices are connected, enabling the seamless flow of data and information? The answer lies in the world of networking. In this blog, we will take you on a journey through the fundamentals of networking, helping you understand the building blocks of our interconnected digital world.
We have reached a state where we live in a connected WORLD, and to be updated with the technology and trends you must be connected. In this blog, we will give you a brief knowledge of Networking and where to start to build a career in Networking.
As you have reached here to my topic, you are already using the network, but how?
While you are accessing this page, either on your desktop/laptop or mobile, using the Internet (Network of networks) via an ISP (Internet Service Provider) you are connected to WWW (Worldwide Web) i.e., Internet. We will get into the Internet a bit later…
How do you get a page (URL), you requested? For e.g., https://www.google.com (A popular search engine)
This includes several stages of communication from your computer system to the computer system having the website (google.com) and one such communication is via HTTPS protocol mentioned in the URL. Now, let’s start from the beginning.
1. How are devices (computers) connected to each other? I prefer mentioning devices instead of computers because, in general, it includes desktops, laptops, mobile, connected cars, smartwatches, and so on.
These are connected to each other using network Topology. Topology is the arrangement that is used to connect computer and network devices. Popular ones are BUS, RING, STAR, MESH.
The pictorial representation is as below:
2. How are these devices identified on a network?
This is done in 2 ways. The first MAC (Media Access Control) address, also known as the hardware or physical address, is given to a NIC (Network Interface Card) by the manufacturer. It is a 48-bit address notation given to card in the format XX:XX:XX:XX:XX:XX, where X can be any digit between 0-9, A-F.
Second, with the use of IP (Internet Protocol) address or logical address. It has version 4 and version 6. This is given by a user/network admin, in the 32-bit binary format (IPv4), typically represented in decimal format A.A.A.A where A can be any decimal number between 0-255. In IPv6 has an address space of 128 bits, represented in 8 blocks of XXXX separated by a colon (:), where each X (hexadecimal digit) corresponds to its binary representation.
Since I have mentioned here about different number systems used in computers, let’s understand these further.
Binary – uses base 2 – Digits are 0 & 1 – used to represent electrical OFF & ON respectively. A combination of these represents information.
Octal – uses base 8 – Digits are 0 to 7
Decimal – uses base 10 – Digits are 0 to 9
Hexadecimal – uses base 16 – Digits are 0 to 9, A to F.
IPv4 address can be grouped into a different class, based on the number in First Octet.
- Class A – starting with number 1 to 126, for e.g., 10.10.10.10, 125.15.145.254
Fixed Subnet mask is 255.0.0.0. - Class B – starting with number 128 to 191, for e.g., 172.25.96.210, 129.0.1.10
Fixed Subnet mask is 255.255.0.0. - Class C – starting with number 192 to 223, for e.g., 192.168.1.1, 201.222.210.22
Fixed subnet mask is 255.255.255.0 - Class D – starting with number 224 to 239. IP addresses in this class are used for multicast.
No subnet mask is required for Class D IPv4 addresses - Class E – starting with number 240 to 255. This class is reserved for experimental purposes.
Did you notice that I have not mentioned the IPv4 address starting from 127? Why is it so?
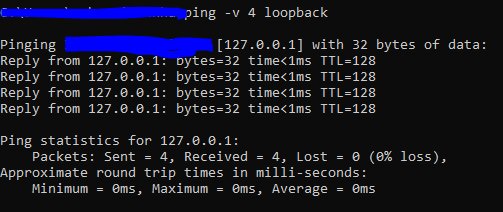
This is a special one, known as Loopback address. i.e., 127.0.0.1. It can be used to check our own network status using the ping utility. A successful response means your NIC is working fine. As shown in the below image.
Further, there are Private IPv4 address and Public IPv4 address.
As the name suggests, Private IPv4 address is free to use and can be used by anyone. These addresses cannot access the internet directly but use Public IPv4 address to do so.
As per the previous classification, Private Address in each class is mentioned in below table:
| Class | Address Range | Default Subnet mask |
| A | 10.0.0.0 – 10.255.255.255 | 255.0.0.0 |
| B | 172.16.0.0 – 172.31.255.255 | 255.255.0.0 |
| C | 192.168.0.0 – 192.168.255.255 | 255.255.255.0 |
IPv4 range not included in the above are Public IPv4 address. These can be obtained from ISPs’.
Some Terminology to Remember
ICANN – The Internet Corporation for Assigned Names and Numbers, is responsible for the maintenance of namespaces and numerical spaces of the Internet.
IANA – Internet Assigned Numbers Authority, responsible for Internet Protocol (IP) addressing systems, and Autonomous System (AS) numbers for routing Internet traffic. It assigns the IP address to RIR as per hierarchy and requirement. There are 5 RIR (Regional Internet Registry) across the Globe.
AFRINIC – Africa Region
APNIC – Asia & Pacific Region
ARIC – Canada, USA & some Caribbean Region
LACNIC – Latin America & some Caribbean Region
RIPE NCC – Europe, Middle East & Central Asia.
Now, we will try to understand about OSI Model.
OSI stands for Open System Interconnection, is a conceptual model designed by ISO (International Organization for Standards), that helps different computer systems irrespective of their manufacturer, model, design to communicate with other systems on a network. This is achieved by characterizing computing functions into a universal set of rules and requirements to support interoperability.
In this 7-layer model, each layer communicates with the same layer at the other end and supports one layer below and above it.
| Layers | Usage | |
| 7 | Application | Serves as a point of Interaction between User and application to access network services |
| 6 | Presentation | Works as a translator for data from session to application. Uses encode/decode, encrypt/decrypt and other data conversion mechanisms. |
| 5 | Session | Control the session-related functions before and after the tasks, viz., establishment, termination, logging, etc. |
| 4 | Transport | Helps in delivery of messages from source to destination, with/without reliability. |
| 3 | Network | Controls the operation of the subnet, decision-making for physical path selection. Contains IP address information |
| 2 | Datalink | Ensure message delivery is error-free from one node to another using the physical layer. Contains MAC address details |
| 1 | Physical | Helps in the transmission of information from source to destination using a wired or wireless medium. Data is transferred in the form of bits. |
Another Standard that is used widely and accepted by all, is TCP/IP (Transmission Control Protocol/Internet Protocol) Model. It was developed by ARPANET (Advanced Research Project Agency Network) by DOD (Department of Defense), hence also referred to as DOD Model. It is a 4-layer Model that goes with the principles defined in OSI 7-layer Model, but with some restrictions. Unlike OSI Layer protocol-independent approach, TCP/IP is protocol dependent. TCP/IP model provides a connection between different computers, whereas the OSI model puts standards in place for devices, like routers, switches, and other hardware. TCP/IP provides a reliable transfer of data between systems.
Below is the table that provides an insight into both OSI and TCP/IP models.
| OSI Model | TCP/IP Model | ||
| 7 | Application | Application/Process | 4 |
| 6 | Presentation | ||
| 5 | Session | ||
| 4 | Transport | Transport/Host-to-Host | 3 |
| 3 | Network | Internet | 2 |
| 2 | Datalink | Network Access/Link | 1 |
| 1 | Physical |
A protocol is a set of rules and standards that should be agreed upon between two devices, for successful communication, and transfer of data.
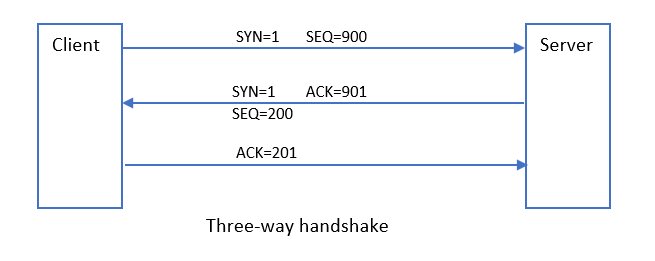
A three-way handshake in TCP/IP communication is a process between client and server system, that exchanges synchronization and acknowledgment packets before the actual data is transmitted over the network. This is the method that ensures reliable communication between systems.
The client starts the communication by sending SYN packet to the server, it wants to communicate, which includes a sequence number (SEQ). Upon receipt of this packet, the server keeps a record of the sequence number, sends back its SYN packet with its randomly generated SEQ number, along with an ACK packet. When the client receives this packet it sends back an ACK packet to the server to complete the 3-way handshake process and start the transfer of data.
In the above diagram, notice how sequence number (SEQ) and acknowledgment number (ACK) are related. This helps the communicating system maintain the order of the data packets received and maintains the reliability of the connection. The communication between the systems is terminated by sending a FIN packet to tear down the connection when it is no longer required.
Now let us again know how to get the URL on our browser.
- User requests a URL using a browser (Application)
- This is sent to the Gateway IP. Private IP cannot access the internet. Gateway helps route information to Public IP obtained from the internet. (NAT process)
- A DNS lookup is performed to get the URL – to – IP conversion. (Internet)
- After getting the desired IP information, a packet establishes a session from your computer to the server hosting the URL.
- After a successful 3-way handshake, a request for the desired page (URL) is sent to the server.
- The server identifies the client requesting the page and returns the information in HTML format.
- This HTML page is then processed at the presentation layer.
- The processed information is then passed to the Browser Application to display the contents of the URL in a human-readable format.
These are a few important processes of many diverse processes.
Hope, this was able to provide you with some basic knowledge of Networking.
Explore More:
- Popular Networking and Hardware Courses
- Most Asked Networking Interview Questions and Answers
- Is CCNA Training the Right Choice for Networking Professionals?
Contributed by - Ashwini Sinha
This is a collection of insightful articles from domain experts in the fields of Cloud Computing, DevOps, AWS, Data Science, Machine Learning, AI, and Natural Language Processing. The range of topics caters to upski... Read Full Bio