What is a Phishing attack?
A cyber attack is an unauthorized attempt to gain unauthorized access to a computer system in order to size, modify, or steal data. Cybercriminals can launch a cyberattack using a variety of attack vectors, including malware, phishing, ransomware, and man-in-the-middle attacks. In this article, we will go over the phishing attack in depth.
Phishing is a social engineering attack that an attacker frequently uses to steal user information such as login credentials and credit card numbers. An attacker impersonates a trusted entity, tricking a person into clicking a malicious link, resulting in malware installation, system freezing as part of a ransomware attack, or the disclosure of sensitive information.
But, before going any further, let’s go through the topics that we will be covering in this blog:
- Impact of Phishing
- Types of Phishing techniques
- How to spot Phishing?
- Case Studies
- Frequently asked questions
Impact of Phishing
Phishing is a type of cyberattack that dates back to the 1990s. Despite being around for decades, it remains one of the most common and damaging cyberattacks. Phishing has two significant consequences:
- Financial loss
- Data loss and legal proceedings
Financial loss
Individuals and businesses alike can suffer devastating financial losses due to Phishing. Individuals’ funds and investments are at risk if hackers gain access to sensitive bank account information. Financial losses for businesses can include regulatory fines and remediation costs, as illustrated by the figures below:
Source: IBM, Retruster, TrendMicro, and Deloitte
Data loss and legal proceedings
Phishing attacks frequently attempt to obtain more than just money from businesses and individuals. They instead attempt to steal something far more valuable – data. When phishing attacks successfully cause data breaches, phishers can cause reputational harm by:
- Using the victim’s information for illegal purposes or blackmailing the victim’s contacts
- Publication of the victim’s personal information in order to embarrass them
- Impersonating the victim in order to send out malicious emails or posts
For businesses, Phishing can result in data breaches that undermine consumer trust. According to a survey, 25% of consumers would lose faith in a company if its data was compromised.
Must Explore- What is Cybersecurity?
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
Types of Phishing techniques
Despite growing awareness and safety measures, many organizations and individuals fall victim to this pervasive scam as phishing messages and techniques become more sophisticated.
We will look at the five most commonly used phishing techniques:
- Link manipulation
- Smishing
- Vishing
- Website forgery
- Pop-ups
- Spear
- Whaling
Link manipulation
Link manipulation involves tricking a user into clicking a link to a fake website. Attackers accomplish this through a variety of channels, such as emails, text messages, and social media.
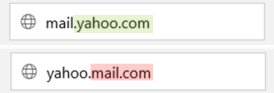
Use of sub-domains: The URL hierarchy is always left to right. If you’re looking for Gmail Mail, the correct URL is mail.google.com, where Google is the primary domain and Mail is the sub-domain. For example, a phisher may trick you with the fraudulent link yahoo.mail.com, which will direct you to a page with the Mail as the primary domain and Yahoo as the subdomain.
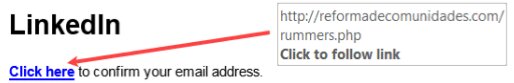
Hidden URLs: When an attacker hides the actual URL of a phishing website under plain text, such as “Click Here” or “Subscribe,” this is known as cloaking. A more convincing scam might even show a legitimate URL redirecting to an unexpected website.
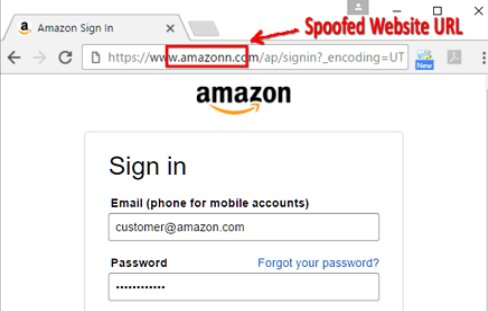
Misspelled URLs: When a hacker purchases domains with misspellings of popular domains, such as facebook.com, google.com, or yahooo.com. This method is also known as URL hijacking or typosquatting.
IDN homograph attacks: A malicious individual uses similar-looking characters to misdirect a user to a link in this technique.
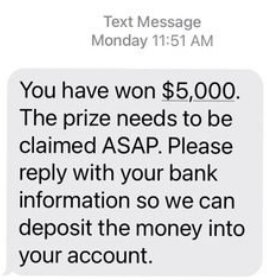
Smishing
Smishing is a type of Phishing in which someone attempts to trick a victim into providing private information via text message. The most common type of smishing is a text message that contains a link that automatically downloads malware. A piece of malware installed on a computer can steal personal information such as banking credentials or tracking locations in order to spread the virus and exponentially multiply.
Must Explore- Who is an Ethical Hacker?
Another smishing technique is to impersonate a legitimate and well-known institution in order to obtain personal information from victims. In some cases, scammers pose as tax authorities in order to get users’ financial information and then steal their money.
Vishing
It is also known as a voice scam and is the telephone equivalent of Phishing. Vishing, like email phishing and smishing, is intended to trick victims into disclosing personal information such as PINs, social security numbers, credit card security codes, passwords, and other sensitive information.
Vishing calls frequently appear from an official source, such as a bank or a government agency. These visitors will even create fake Caller ID profiles to make the phone numbers appear legitimate. Nowadays, attackers impersonate people by mimicking voices with artificial intelligence and tricking victims into transferring money to them.
Website forgery
Website forgery works by having a malicious website impersonate a legitimate one in order to trick visitors into giving up sensitive information such as account numbers, passwords, and credit card numbers. Attackers primarily accomplish web forgery through two methods:
- Cross-site scripting
- Website spoofing
Cross-site scripting: This happens when a hacker exploits a vulnerability, and after that, they execute a malicious script into a legitimate web application or website.
Website spoofing: Attackers accomplish this by creating a fake website that appears to be identical to the legitimate website that the user wishes to access.
Pop-ups
Aside from being annoying, pop-up messages are one of the simplest ways to conduct phishing scams. They enable hackers to steal login information by displaying pop-up messages to users and eventually redirecting them to bogus websites. There are two variants of this technique:
In-session phishing: This type of phishing operates by displaying a pop-up window during an online banking session and prompting the user to retype his username and password because the session has expired. The user enters his information, not suspecting that the pop-up is a scam because he has already logged into the bank’s website.
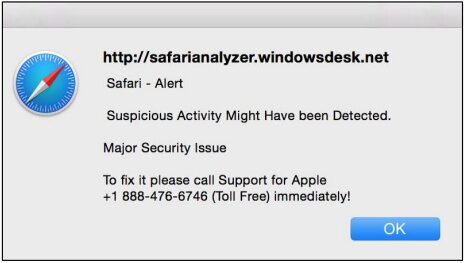
Pop-up tech support: Another common pop-up phishing scam is “popup tech support.” While browsing the Internet, you get a pop-up message informing you that your system has been infected and that you should contact your vendor for technical support.
Spear
Instead of a large group of people, spear phishing targets specific individuals. Attackers commonly carry out victim research on websites and social media. This allows them to personalize their communications and appear more genuine. Spear phishing is commonly used as the first step in breaching a company’s defenses and carrying out a targeted attack.
Whaling
Whaling takes place when an attacker goes after a “big fish,” such as a CEO. These attackers frequently devote significant time to profiling the target in order to find the best opportunity and method of stealing login credentials. Whaling is especially concerning because high-level executives have access to a wealth of company information.
How to spot Phishing?
Mismatched and misleading data: Pay attention to domains/subdomains, misspellings, and similar-looking URL characters. Glide your mouse pointer over a dubious link to see the real URL over a suspicious link.
Use of urgent or threatening language: Phishers frequently use phrases like “urgent action required” or “your account will be terminated” to instill panic and fear in order to trick you into providing confidential information.
Promises of attractive rewards: False promises of amazing deals or unbelievable prizes are commonly used to instill a sense of urgency in providing your confidential information. If something appears too good to be true, it most likely is.
Requests for confidential information: Most legitimate organizations will never ask you for personal information such as your login credentials or credit card information.
Unexpected emails: Do not open attachments or links if you receive an email about a purchase you did not make.
Suspicious attachments: Use caution and watch for unusual attachment names and file types. Be especially cautious of.exe files and delete them immediately if they appear unexpectedly in your inbox.
Case Studies
Some of the famous incidents are:
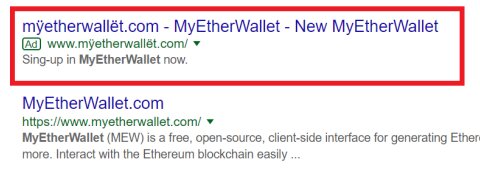
2017 Ethereum Classic
Following the hacking of the Ethereum Classic website in 2017, several people lost thousands of dollars in cryptocurrency. Hackers scammed Classic Ether Wallet’s owner, thus gaining access to the domain registry, then redirected the domain to their own server, where they extracted Ethereum cryptocurrency from victims.
Google Docs, 2017
In May, phishers sent out fraudulent email invitations on Google Docs inviting recipients to edit documents, forcing over 3 million workers worldwide to stop working. When recipients opened the invitations, they were directed to a third-party app that allowed hackers to access individuals’ Gmail accounts.
Conclusion
Phishing is a form of scam in which an attacker poses as a legitimate entity or person via email or other forms of communication. Phishing emails are frequently used by attackers to distribute malicious links or attachments that can perform a variety of functions.
Recently completed any professional course/certification from the market? Tell us what liked or disliked in the course for more curated content.
Click here to submit its review with Shiksha Online.
FAQs
How can you avoid being a victim of phishing?
There are many steps that you can take to avoid phishing, such as using security software to safeguard your computer, setting your phone's software to automatically update to protect it, using multi-factor authentication to secure your accounts, and backing up your data to protect it.
How do you distinguish between spam and phishing?
Spam is unsolicited email, such as instant messages or social media messages, whereas phishing is an email sent by an Internet criminal posing as a legitimate or trustworthy source.
Does antivirus protect against phishing?
Antivirus software can detect and block phishing emails that come from a suspicious source that an attacker commonly uses in phishing attempts.
What are the consequences of phishing?
Phishing has a number of negative consequences, such as financial loss, intellectual property infringement, and reputational harm.
What are the most common phishing tools used by attackers?
An attacker can use a variety of phishing tools, such as Infosec IQ, Gophish, LUCY, Simple Phishing Toolkit (sptoolkit), Phishing Frenzy, and others.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio