Ransomware: How It Works and How To Get Rid Of It?
Ransomware is a widespread and dangerous form of malware. It has the potential to impact both organizations and individuals. Ransomware attacks can have a significant impact on business processes and end up leaving organizations without any of the data they require to operate and provide services.
So, what exactly is ransomware? We will discuss this briefly in this article. But, before moving on that, let’s go through the topics that we will be covering in this article:
- What is ransomware?
- How does it work?
- Real-life examples of ransomware attacks in India
- Common types of ransomware variants
- Methods for determining whether or not your system is infected with ransomware
- How to remove ransomware from your computer
- How to protect against ransomware
- Conclusion
What is ransomware?
Ransomware is a malware designed to prevent a user or organization from accessing files on their computer. Attackers encrypt these files and expect payment for the decryption key as a ransom. Compensation for the decryption key can vary from a few hundred dollars to millions of dollars, receivable in Bitcoin. Individuals or organizations may believe that paying the ransom is the easiest and most effective way to regain access to their files. There is no guarantee, however, that the attacker will keep their word.
You can also explore- What is Cybersecurity?
Due to the covid situation, more people are working from home and taking advantage of this fact; hackers have increased their use of phishing, a common entry point for ransomware infection. Because of the ease with which ransomware can be spread via email, it is among one of the most common malware attacks.
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
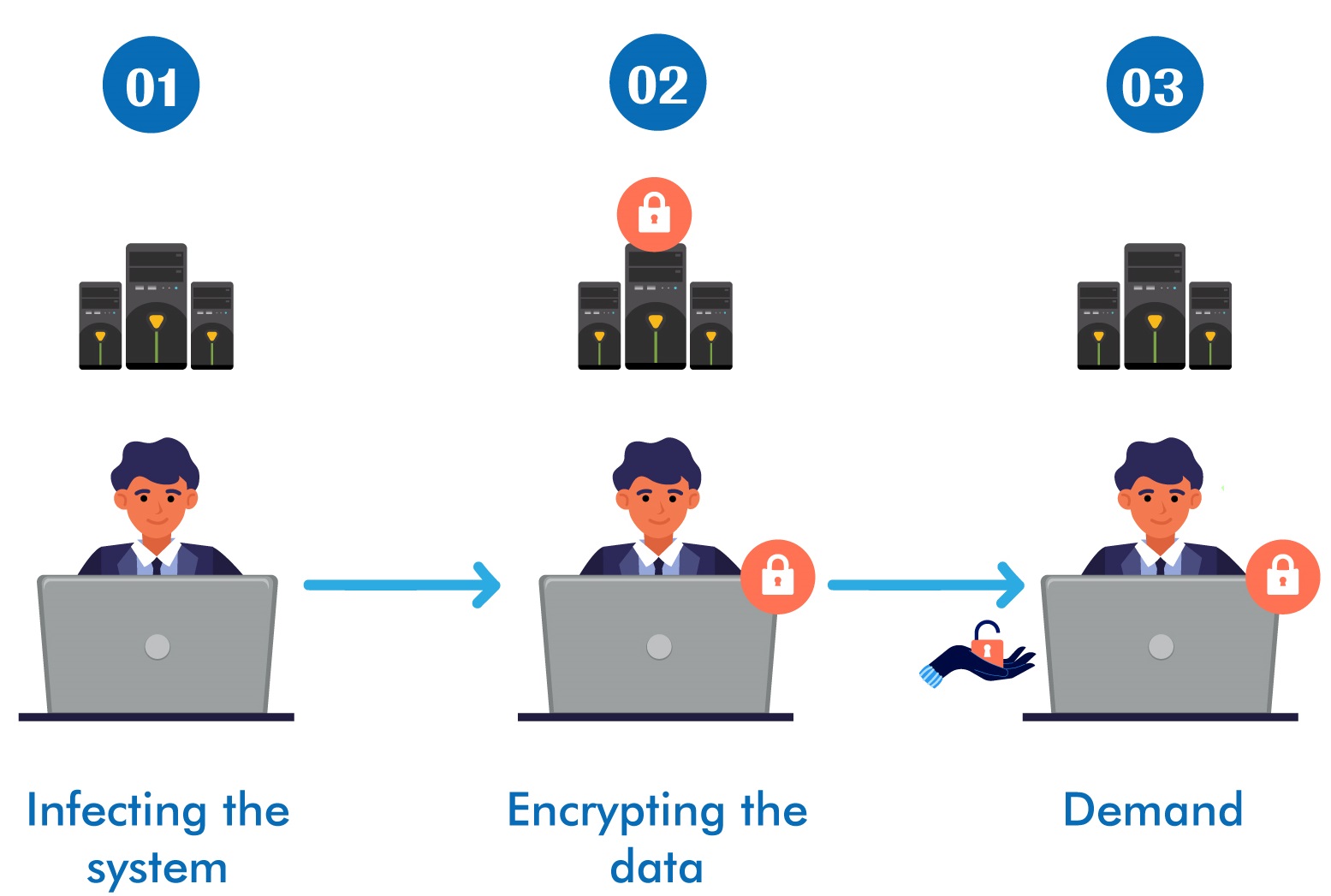
How does it work?
It will be simple to explain the operation of ransomware in stages. As a result, the overall operation consists of three stages:
Infecting the system: Phishing spam is among the most common delivery systems. In this case, the victim receives attachments in an email that appear to be a file they should trust. Once downloaded and opened, they have the ability to take over the victim’s computer. Attackers can also employ the remote desktop protocol (RDP). An attacker can use remote desktop protocol (RDP) to remotely access a computer within the enterprise network and drop the payload if they have stolen or guessed an employee’s login credentials.
You can also explore – What is a Phishing attack?
Encrypting the data: Once an attacker has gained access, the second stage begins encrypting the data. An attacker encrypts the data in order to block access to data or a computer system.
Demand: After completing the above two stages, the third stage starts. Once the attackers have infiltrated the system and encrypted the data, the attackers ask for a ransom to decrypt the data or not to publish it online. Mostly, this amount is given to the hacker in the form of bitcoin as bitcoin transactions are not traceable.
Real-life examples of ransomware attacks in India
Some of the real-life examples are:
- The Uttar Haryana Bijli Vitran Nigam was impacted by a ransomware attack in which attackers gained access to their computer systems and stole customer billing data. The attackers demanded Rs.1 crore in exchange for the data.
- The Petya ransomware attack halted work at one of India’s busiest seaport terminals, resulting in a computer lockdown and severe consequences for the country’s exports.
Common types of ransomware variants
There are various types of ransomware variants. Some of the most common are:
Bad Rabbit: It is a variant that has infected organizations in Russia and Eastern Europe. On compromised websites, Bad Rabbit spreads via a bogus Adobe Flash update. When this variant infiltrates a machine, it redirects users to a payment gateway that demands 0.5 bitcoin.
You can also explore – All about Bitcoin Blockchain
Crysis: This variant uses a robust encryption algorithm to encrypt files on fixed, detachable, and network drives, making it much more challenging to break in a decent amount of time. It spreads through emails that contain attachments.
CryptoLocker: It is an encryption Trojan horse virus. An attacker encrypts the files and decryption requires the user to buy a passcode.
You can also explore – What is a Trojan horse attack?
KillDisk: It is a Linux-specific variant. This variant undermines businesses by removing files and modifying files at random. KillDisk does not save the encryption key on the disc or online, making file recovery complicated without paying compensation.
GoldenEye: This variant spreads via a sizeable social engineering campaign. Whenever a user installs a GoldenEye-infected file, a macro is launched that encrypts data on the victim’s computer.
Locky: It is another variant that locks the victim’s computer and prevents them from using anything until they pay a ransom. It spreads through emails.
KeRanger: It is a Trojan horse ransomware virus that is the first to target Mac OS. It is an encryption virus that seeks to prevent access to your critical documents unless you pay an amount.
WannaCry: This is the most well-known variant around the world. This variant infected over 125,000 organizations in 150 countries. WCry and WanaCrypt0r are two alternative names for the WannaCry variant .
Methods for determining whether or not your system is infected with ransomware
Some of the ways to check whether or not your system is infected with ransomware are:
- Antivirus: Using an antivirus can help you detect ransomware. You should use antivirus to scan your system often so that if it’s infected, you can take preventive measures in the early stage. Antivirus can detect ransomware until and unless it has been bypassed.
- Check the file extension: Users can verify the file extension. For example, an image file’s normal extension is “.jpg” or “.png“. There could be a ransomware infection if this extension changed to a new and unknown combination of letters.
- Increased CPU activity: An increase in CPU activity could indicate that ransomware is active in the background.
- Different names: You may notice that files have names that differ from those you assigned. When the ransomware encrypts data, it frequently changes the file name.
- Encrypted files: Unable to open files is a late sign of ransomware activity.
How to remove ransomware from your computer
Here are the steps to remove ransomware from your computer are:
- Isolate infected devices (Step 1): The first step is to turn off your computer’s internet connection. This will keep ransomware from infecting other network devices.
- Make a backup of your system (Step 2): An encrypted backup is preferable to no backup. Make a backup of your data.
- Disable system optimization software (Step 3): You may need the ransomware files for diagnostics, so disable any software that may unintentionally delete them.
- Determine the type of ransomware (Step 4): The next step is to determine what type. Because the procedures for removing different types of ransomware vary, resolving the problem is easier if you know what you’re dealing with.
- Remove ransomware (Step 5): You can remove it by using powerful cybersecurity software or manually restoring your system.
- Recover your encrypted files (Step 6): Now that you have removed the underlying malware, it’s time to recover your encrypted files.
How to protect against ransomware
Some methods for avoiding ransomware include:
- For all critical data, use a data backup and recovery plan. You should perform and test regular backups to minimize the impact of data.
- It would be best if you did not allow macros from email attachments. If somehow the user opens the attachment and permits macros, embedded code on the machine will execute the malware.
- Limit users’ permission to configure and run unwanted software applications. These restrictions may help stop ransomware from operating or restrict its power to spread across the network.
- Update your operating system and software with the most recent patches. Most attacks target defenseless applications and operating systems.
- Do not click on unsolicited email Web links.
- Keep anti-virus software up to date, and scan all downloaded applications before running it.
Conclusion
I will not recommend paying the ransom as there is no guarantee that the attacker will keep his word and provide you with the decryption key. To avoid all this in the first place, it is preferable to take the preventive measures outlined above rather than being sorry later!!
FAQs
Is it possible for ransomware to spread without the Internet?
Yes, ransomware can infect any network-connected device, including external hard drives. But, if that external drive is not connected to an infected device, ransomware cannot infect it wirelessly.
What are the two primary anti-ransomware defenses?
To ensure maximum security, use reputable anti-malware software and a firewall. You can also implement a patch management policy to ensure that all systems receive the most recent software updates.
Can ransomware steal information?
Yes, data theft is now a standardu00a0component of ransomware attacks.
Why do cybercriminals use ransomware?
Hackers use ransomware to prevent users from accessing data on their computers by encrypting files. Once the information is encrypted, the hacker can demand money for the decryption key.
What is the most common method of ransomware distribution?
The most common method is phishing emails with malicious attachments.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio