What Is Social Engineering and How Does It Work?
Humans are the most vulnerable point in a cybersecurity strategy. With the rapid advancement of technology, hackers are devising ever-more devious methods of duping employees and individuals into handing over valuable data. Social engineering is one such method.
But what exactly does social engineering means? Let’s go over the topics we’ll be covering in this article before we answer that question:
- What is social engineering?
- Social engineering attacks
- How does social engineering work?
- Real-life cases related to social engineering attack
- Why is social engineering attack so dangerous?
- Who are the common victims of this attack?
- How to prevent social engineering?
- Conclusion
What is social engineering?
In the context of cybersecurity, social engineering is an attack that heavily relies on human interaction and usually includes tricking people into breaking standard security protocols and disclosing private information and best practices. An attacker can use all this information to his advantage or launch a successful cyberattack.
You can also explore- What is cybersecurity?
An attacker can use social engineering not only to steal someone’s identity, compromises their credit card and bank account, but also to obtain a company’s trade secrets or exploit national security. Attackers use social engineering tactics because it is usually easier to exploit a human’s natural tendency to trust than to explore ways to penetrate your software.
It is far easier to trick someone into giving you their password than trying to hack their password. Hackers and scammers understand that regardless of how strong your password is, there is one weakness they can always exploit: “You”. Social engineering attacks exploit the “human loophole” to circumvent cybersecurity barriers.
Let’s look at an example to help you understand it better. Assume an attacker contacts the customer service department of an email provider to request a password reset for their account. The account, however, does not belong to the attacker. The attacker persuades the service provider to reset the password, allowing the attacker to control the target’s email account instead of hacking into it.
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
Social engineering attacks
Social engineering is a broad term that refers to various manipulation techniques that hackers can use to obtain information. Some of the types of attacks that fall under the social engineering attack category are:
Baiting: It is an attack in which the attacker tempts entices the victim to click on a link with a freebie. This could be free music, gift cards, a movie, or anything else. When an unaware user clicks on the link, they are infected with malware.
Phishing: It is an attack in which a criminal pretends to be a trustable entity in order to trick a person into clicking on an infected link, which results in malware installation, system freezing, or even the release of sensitive data.
Scareware: In this type of attack, an attacker bombards a target with false threats or alarms in the hopes that their natural desire to protect themselves or something they value will drive them to take the desired action.
Pretexting: This attack occurs when an attacker lies to the victim about their identity. They trick the target into handing over sensitive information after gaining their trust.
Vishing: It is an attack in which an attacker uses a social engineering technique over the phone to obtain financial or personal information from the target.
Diversion theft: This attack occurs when attackers use the social engineering technique to trick a delivery or courier company into going to the incorrect pickup or drop-off location, intercepting the transaction.
USB baiting: In this attack, an attacker installs malware on a USB and puts or leaves them in prime places, hoping that an individual will pick up the USB and insert it into a commercial environment, unknowingly releasing malicious script into their organization.
Honey trap: It is a type of social engineering strategy in which an attacker baits a victim into a sexually vulnerable situation. The attacker then takes advantage of the situation to blackmail the victim.
How does social engineering work?
Social engineering works by exploiting people’s cognitive biases. An attacker disguises themselves as a trustworthy or an authoritative individual and dupes the victim into trusting them. Once the victim believes the attacker, they are duped into disclosing personal information.
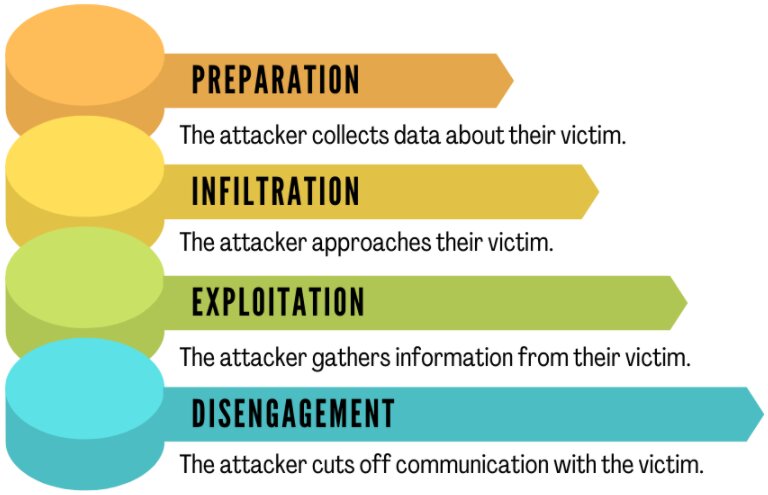
The working of a this attack can be explained by dividing the overall process into four steps. Those four steps are:
- Preparation: The attacker collects data about their victims, such as where they can reach them via social networks, emails, messaging apps, etc.
- Infiltration: The attacker approaches their victims, generally imitating a reliable source and utilizing the victim’s information to validate themselves.
- Exploitation: The attacker uses persuasion to gather information from their victim, such as email address, login credentials, etc.
- Disengagement: The attacker cuts off communication with their victim, launches an attack, and flees.
Real-life cases related to social engineering attack
Case1:
In 2019, Toyota Boshoku Corporation, an automotive parts supplier, became a victim of social engineering attack. Attackers used persuasion to convince a finance executive to alter a user’s account details in a money transfer.
Case2:
In 2020, a Shark Tank television judge, Barbara Corcoran, was duped in a nearly USD 400,000 social engineering scam. A fraudster posing as her assistant sent an email to the accountant requesting a real estate investment renewal payment. The accountant inquired about the payment via email to the assistant’s correct address, thus noticing the attack.
Case3:
In 2022, Bleeping Computer mentioned an advanced phishing attack to obtain Office 365 credentials. The attackers impersonated the US Department of Labor (DoL) in the attack. The emails were professionally written and were using official DoL branding. With the help of this email, attackers invited receivers to bid on a government project.
The email contained a three-page PDF with an embedded “Bid Now” button. Targets were redirected to a phishing site after clicking the link. The fake bidding site instructed users to enter their Office 365 credentials, allowing the credentials to be stolen.
Why is social engineering attack so dangerous?
We can all agree on one thing: emotions and humans are unpredictable, which makes social engineering especially dangerous. It relies solely on human error rather than flaws in software and operating systems.
Legitimate user errors are much less predictable, making them more challenging to identify. Victims may be unaware that an attacker has tricked them during or after the attack.
Who are the common victims of this attack?
Most victims of social engineering attacks are:
- Individuals of high worth, employees, or leaders: Criminals prey on people with easy access. The rule is simple: the more access someone has to what attackers want, the more and more appealing that target becomes.
- Popular online personalities: Individuals who disclose more personal information via the internet are much more likely to be the targets.
- Employees who are unaware of cybersecurity threats: According to one study, 16% of employees worldwide are unaware of any cybersecurity attacks.
How to prevent social engineering?
Some of the most common ways to prevent a social engineering attack are:
Multi-factor authentication: The attackers can gain your passwords by using social engineering techniques. Hence, multi-factor authentication is necessary, and it can be anything from biometric access and security questions to an OTP code.
Verify the identity of the email sender: Most scams involve falsely obtaining victim information by posing as a trusted entity. To avoid such threats, contact the purported author of the email message and verify whether or not he sent the email.
Always look for an SSL certificate: When entering sensitive information on a website. Examine the URLs to ensure the website’s authenticity. URLs that begin with https:// provide a secure connection, whereas websites that begin with http:// do not provide a secure connection.
Leave a smaller digital footprint: Oversharing of personal information on social media can provide criminals with more information to work with. In my opinion, you should keep your social media settings to “friends only” and think twice before sharing anything on social media.
Penetration testing: You can perform a penetration test to detect and attempt to exploit vulnerabilities. With this, you can also identify different types of social engineering attacks to which you may be vulnerable.
Check and update your security patches: When companies discover security flaws, they issue security patches as a response. As a result, keeping your systems up to date will reduce the likelihood of cyberattacks.
Enable spam filtering: Most email service providers provide spam filters that grab emails that are considered suspicious, and with spam functionalities, you can easily categorize emails.
You can also explore – What is Safe Browsing & How to Turn It On?
Conclusion:
The dangers of social engineering threats are growing by the day, and they are now one of the most severe cyber threats to individuals and businesses of all sizes. Make sure you use the prevention techniques discussed above because it is better to be safe than sorry later!
FAQs
What information can be obtained through social engineering?
Using this scam, an attacker obtains various information and records, including Aadhar numbers, personal phone numbers, addresses, bank records, etc.
How does social engineering attack work?
Social engineering attacks are relatively straightforward. A hacker must convince one under-informed, stressed, or trusted person to do what they say.
What exactly is a digital footprint?
It is a collection of data from online actions and communications that can be traced back to an individual.
What are the most common types of social engineering attacks?
Some of the most common types of social engineering attacks are: Phishing Scareware Watering hole Whaling DNS spoofing Pretexting
What are the foundations of social engineering attacks?
Social engineering attacks rely heavily on human interaction and frequently involve people's manipulation.
What is the frequency of social engineering attacks?
According to a report and information security experts, social engineering techniques are used by cybercriminals in 98 percent of attacks.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio