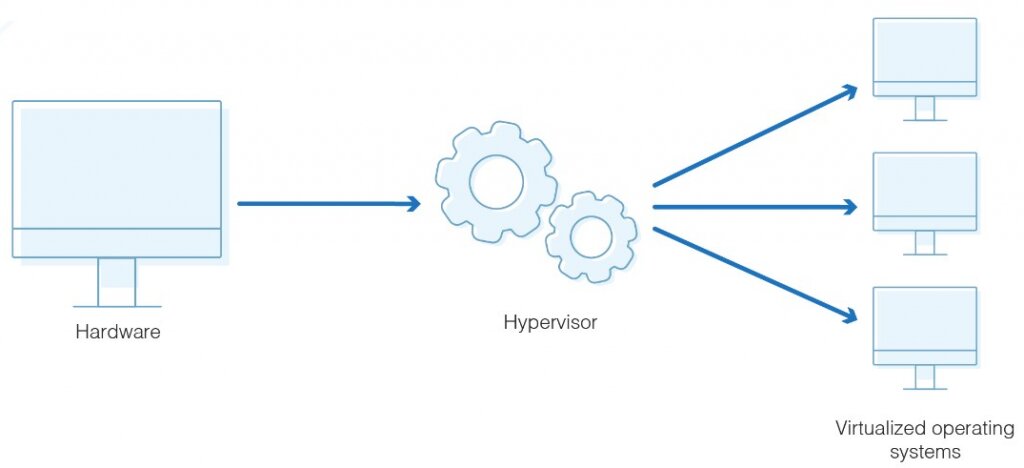
The hypervisor in cloud computing
The hypervisor creates a virtual platform on which various guest OS are implemented and controlled on the host computer.
A hypervisor is also known as a VMM (virtual machine monitor). It is software that creates and handles virtual machines. A hypervisor allows a single host computer to support various guest virtual machines. The hypervisor virtually shares its resources, such as memory and processing. This article focusing on hypervisor in cloud computing.
You can quickly reallocate the hypervisor views resources such as CPU, memory among current guests, or new virtual machines.
In this article, we will go over hypervisors in a nutshell. But first, let’s go over the topics we’ll be covering in this blog:
- How does a hypervisor work?
- Types
- Why use a hypervisor?
- Benefits
- Hypervisor security
- Hypervisor reference model
How does a hypervisor work?
In a business setting, hypervisors and collections of virtual machines are used for various tasks such as data replication. Typically, if you want to replicate a virtual machine, you must copy its entire volume manually. You can use it to select which virtual machines and components you would like to replicate.
Suppose you own a company with multiple servers that provide various services to customers via the internet. Then, it cannot be easy to centrally handle them all, particularly those running different operating systems. A hypervisor allows you to virtualize these servers and manage them all in one physical machine, making them more efficient.
In simple terms, you can allocate resources to all machines. Making better use of the total physical resources available instead of having physical resources shut down when they’re not in use.
Desktop virtualization is beneficial once you want to use software compliant with one OS, but your machine has another OS. You can use a hypervisor to create a Windows virtual machine to run the software without changing operating systems.
Best-suited AWS Certification courses for you
Learn AWS Certification with these high-rated online courses
Types
There are two types:
- Type-1: bare-metal or native
- Type-2: hosted or client
Type 1: This type of hypervisor runs on the server directly. You can manage guest operating systems with bare-metal hypervisors. This is the most common hypervisor used for data center computing needs.
In general, this type of hypervisor outperforms hosted hypervisors. Examples of bare-metal hypervisors include Xen, Citrix XenServer, etc.
Check Out the Best Online Courses
Type 2: This type of hypervisor runs as a software layer on top of the OS of the host machine. They help in abstracting guest operating systems from the host OS. Examples of hosted hypervisors include QEMU, VMware Fusion, etc.
Why use a hypervisor?
The guest VMs does not use the host hardware. As a result, hypervisors allow the use of more of a system’s available resources and provide greater IT mobility. This means you can easily transfer them between servers. Because hypervisors allow multiple virtual machines to run on a single physical server, it reduces:
- Maintenance requirement
- Space
- Energy
Benefits
There are many benefits of hypervisors. Some of those benefits are:
Portability: Applications that experience spikes in demand can simply connect to additional machines to scale as needed. This is possible because hypervisors allow workloads to move between VMs. Moving workload between a VM and an organization’s on-premises hardware is also possible.
Utilization: Hypervisors allow multiple virtual machines (VMs) to run on a single physical server and share resources. Thus, increasing server utilization while saving on power, cooling, etc.
Flexibility: The hypervisor guest VMs and OSs run on a wide range of hardware.
Time to use: Cloud hypervisors allow virtual machines (VMs) to be instantly turned up or down. This will enable projects to be created and teams to work on the same day. When a project finishes, you can terminate the VMs. This saves organizations money on infrastructure that isn’t necessary.
Reliability: Hardware failures can be remedied by moving virtual machines to different machines.
Hypervisor security
Hypervisors add an extra layer of protection between an operating system and online resources. Even if a resource causes problems within a VM, the hypervisor guards the primary host and operating system.
Suppose a hacker gains unauthorized access to a hypervisor or its management software. Then they can gain access to every VM controlled by the hypervisor as well as the data contained within them. It prevents intrusions during the development and implementation stages.
Hypervisor security covers:
- Use of network security and monitoring tools
- Setting appropriate access privileges
- Reducing the attack surface
- Keeping the hypervisor updated and patched
This allows IT administrators to continuously monitor their environment and detect abnormal or unusual behavior. Now we arrive at the more critical question of whether hypervisors can improve cloud computing security.
Explore Free Online Courses with Certificates
A hypervisor is a frequent target of hackers. It controls all of the hardware resources while managing all of the virtual machines that reside on it. The bad news is that it is vulnerable to a range of malicious code—particularly that from a hostile virtual machine.
Hypervisor reference model
The three central module coordinates are:
Dispatcher:
The dispatcher acts as the monitor’s entry point. Its job is to reroute the virtual machine instance’s instructions to either of the two modules.
Allocator:
The allocator is in charge of determining which system will allocate system resources to the virtual machine instance. It means that whenever a virtual machine attempts to execute an instruction that changes the machine resources, the dispatcher invokes the allocator.
Interpreter:
The interpreter module consists of interpreter routines. When a virtual machine executes a privilege instruction, these are executed.
In Conclusion
A hypervisor is beneficial for managing virtualization in systems and for efficiently managing work in different operating systems. A hypervisor is responsible for all management and support, so choosing the right one is critical. Though the initial setup is costly, it is profitable in the long run.
If you want to learn more about AWS resources or services you can refer to these articles:
Recently completed any professional course/certification from the market? Tell us what liked or disliked in the course for more curated content.
Click here to submit its review with Shiksha Online.
FAQs
Which hypervisor type is more secure?
Type I hypervisors are safer than type II hypervisors.
What are the advantages of using a hypervisor?
You can successfully run and monitor concurrent virtual machines on a host with a hypervisor.
What exactly is a cloud hypervisor?
A cloud hypervisor is a software that allows multiple virtual machines to share a cloud provider's physical compute and memory resources (VMs).

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio