What are Different Types of Cryptography?
Nowadays, every human activity revolves around computing systems. We are using this computing technology in various applications, such as healthcare, education, banking, software, marketing, etc. However, you may be wondering how organizations protect their data. The answer to this question is “Cryptography.”
Table of Content
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
What is cryptography?
Cryptography is the science of concealing information so that no one else can see it except the intended recipient. The cryptographic practice entails using an encryption algorithm to convert plaintext to ciphertext. The receiver deciphers the ciphertext text using a shared or determined key.
You can also explore- What is Cybersecurity?
Cryptography employs various algorithms, also known as ciphers, to perform encryption and decryption. These algorithms are a complete set of instructions consisting of computations that render various properties of a standard cryptosystem. Some guarantee non-repudiation and integrity, while others guarantee privacy, security, and authentication.
Types of Cryptography
There are three types of cryptography:
- Symmetric key cryptography
- Asymmetric key cryptography
- Hash Function
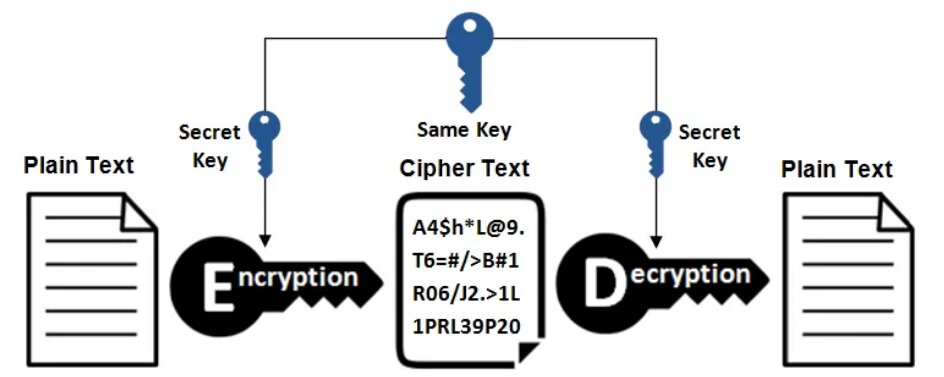
Symmetric Key Cryptography
Symmetric key cryptography is also known as secret-key cryptography, and in this type of cryptography, you can use only a single key. The sender and the receiver can use that single key to encrypt and decrypt a message. Because there is only one key for encryption and decryption, the symmetric key system has one major disadvantage: the two parties must exchange the key in a secure manner. An example of symmetric key cryptography is Blowfish.
You can also explore- What is phishing?
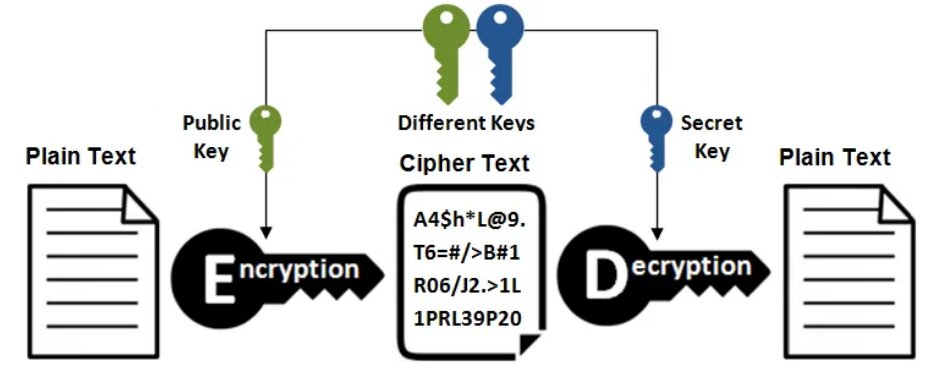
Asymmetric Key Cryptography
Asymmetric key cryptography is also known as public-key cryptography, and it employs the use of two keys. This cryptography differs from and is more secure than symmetric key cryptography. In this system, each user encrypts and decrypts using two keys or a pair of keys (private key and public key). Each user keeps the private key secret and the public key is distributed across the network so that anyone can use those public keys to send a message to any other user. You can use any of those keys to encrypt the message and can use the remaining key for decryption. An RSA algorithm is an example of asymmetric key cryptography.
Hash Function
This algorithm makes no use of any keys. A hash value with a fixed length is calculated based on the plain text, making it impossible to recover the plain text’s contents. Many operating systems encrypt passwords using hash functions.
Types of Cryptography Algorithm
Cryptographic algorithms are primarily of two types, and you can use them for critical tasks, such as authentication, data encryption, and digital signatures.
RSA: RSA is an asymmetric cryptographic algorithm based on the block cipher principle. It converts plain text to ciphertext at the receiver end and vice versa. If we use User A’s public key for encryption, we must use the same user’s private key for decryption.
For more information, you can also explore: Do You Know: What Is a RSA Algorithm?
DES: Data Encryption Standard (DES) is a symmetric cipher algorithm that encrypts and decrypts data using the block cipher method. The algorithm uses 48-bit keys to convert the plain text in 64-bit blocks into ciphertext. It operates on the Fiesta Cipher Structure.
You can also explore- Who is an Ethical Hacker?
Examples of Cryptography
End-to-end encryption in WhatsApp is a prominent example of cryptography encryption these days. This feature is available in WhatsApp via the asymmetry model or public key methods. Only the intended recipient is aware of the actual message. After the WhatsApp installation, the server registers the public keys, and messages are transmitted.
Digital signatures are the next real-time application of cryptography. When two clients must sign documents for a business transaction. However, if two clients never meet, they may not believe each other. The use of encryption in digital signatures then ensures improved authentication and security.
For more information, you can also explore: What is a digital signature?
How Does Cryptography Work?
Cryptographic algorithms are central to how cryptography works. Cryptographic algorithms, also called ciphers, are mathematical functions that encrypt text by combining them with keys such as phrases, digits, words, and so on. You can define the effectiveness by the strength of the cryptographic algorithms and the level of key secrecy.
Applications of Cryptography
There are various applications of cryptography. Some of those applications are:
Confidentiality: Cryptography allows users to store encrypted data, avoiding the major flaw of hacker circumvention.
Non-repudiation: The creator/sender of information cannot later deny his intent to send information.
Authentication: Helps to authenticate the sender and receiver’s identities along with the destination and origin of the information.
Integrity: Information cannot be altered during storage or in transit between the sender and the intended receiver without any addition to the information being detected.
Conclusion
In today’s world, information is primarily available in digital format. Critical information is now digitally recorded, analyzed, and transferred via computer systems. Because information is so essential, attackers target computers to gain unauthorized access. This is where cryptography comes into play. Cryptography offers a scalable set of techniques that guarantee disruption of the attacker’s malicious intentions while legitimate users have access to data.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio