What is a Virtual Private Network (VPN)?
VPN is beneficial if you want to torrent anonymously, access the dark web, or keep your important information secure. As a result, third parties will find it more challenging to track your online activities and steal data. So, what exactly is VPN?
This article will cover Virtual Private Network (VPN) in great detail. But, before proceeding, let’s go through the topics that we will be covering in this blog:
- What is VPN?
- Types of VPN
- Virtual Private Network’s encryption protocols
- Working of VPN?
- Advantages of using a VPN connection
- How to choose the right VPN?
- How to set up a VPN?
What is VPN?
A virtual private network creates a secure, encrypted connection, allowing you to browse the internet and conduct online transactions while safeguarding your data and identity. A virtual private network is now used by up to a quarter of all internet users as essential security software. By using a virtual private network, you can browse the internet and work online while remaining safe and limited. A virtual private network is like your own private internet lounge, where you would hang around without being bothered by other people. There are various popular VPNs, such as PIA, ExpressVPN, etc.
You can also explore – What is Wireless Networking?
VPN makes you virtually unnoticeable and provides access to the media and websites that you would not have access to otherwise. Some governments, for example, may require ISPs to block access to websites they do not want their citizens to see.
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
Types of VPN
Remote access VPNs, personal VPNs, mobile VPNs, and site-to-site VPNs are the four main types of virtual private network services.
Remote Access VPNs
Client-based VPNs or client-to-server VPNs are other names for remote access VPNs. A remote access virtual private network allows you to connect to a private network via the internet, such as your company’s office network. The internet is an untrustworthy communication channel. VPN encryption protects and secures data as it travels to and from the private network.
A remote access virtual private network example – A home worker could connect to the company’s network using a remote access VPN. Their computer works as if it is connected to the company network in the office, and data is secure as it travels through the public internet.
Personal VPNs
A personal VPN service joins you to a VPN server, which acts as a go-between for your device and the internet platforms you want to use. This virtual private network secures your connection, hides your online identity, and allows you to create a fake geographic location. Personal VPNs are usually sold on a monthly subscription basis. A personal VPN service, as opposed to a remote access VPN, does not provide access to a private network.
Streaming movies and TV shows videos that are unavailable in your geographic location is an example of a personal virtual private network service. For example, you can connect to a VPN server in the United States and access American Netflix, which has one of the largest content libraries on Netflix.
Mobile VPNs
A mobile VPN maintains connection even if the user changes WiFi or cellular networks, loses connectivity, or turns their device off for an extended period. An example of mobile VPN- Firefighters and police officers can use a mobile virtual private network to stay connected to applications, such as car registration databases, while on the move.
Site-to-Site VPNs
A site-to-site VPN allows you to connect two different networks in the same or different organizations in the same or different regions. An example of a site-to-site VPN- if a company has two offices on the east and west coasts, You can use a site-to-site virtual private network to connect them to a single network. Network-based VPNs are another name for site-to-site VPNs. Intranet and Extranet are the two types of site-to-site VPN.
Once the connected networks are from the same company, the combined VPN is intranet-based. Whereas, when the connected networks are from different companies, the combined VPN is extranet-based.
Virtual Private Network’s encryption protocols
There are various VPN encryption protocols, such as:
OpenVPN: It is the most widely used encryption protocol. One of its main advantages is that it is highly configurable. It also provides a good balance of speed and security because you can use it on both TCP and UDP ports.
IKEv2: It is a tunneling protocol that you can typically use in conjunction with IPSec for encryption. It has numerous advantages, including restoring a secure connection after the internet goes down. It also evolves well to modify network configurations.
L2TP: Layer 2 Tunneling Protocol is a data transmission protocol that allows data to be transferred from one device to another. Because L2TP does not provide encryption, it is almost always used in conjunction with IPSec.
PPTP: It is the most widely used protocol, with thousands of operating systems and devices supported. It’s also simple to set up, as no additional software is required.
SSTP: As this can bypass most firewalls, Secure Socket Tunneling Protocol is a viable substitute for conventional protocols in areas where VPNs are prohibited.
You can also explore – What are the Different Types of Network Topology?
Working of VPN?
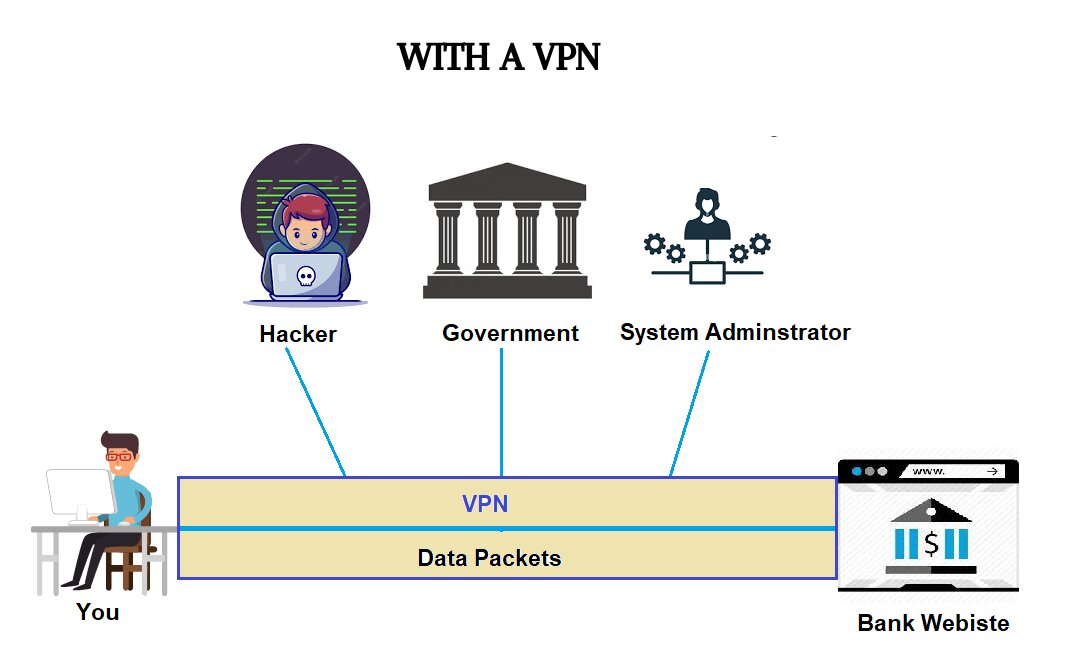
A virtual private network connects you to the internet while acting as a bridge between you and the internet. Instead of communicating directly with a website, you would use a VPN server, primarily to keep your internet activity strictly confidential.
Assume you want to transfer money from a bank account to a family member’s account. To do so, you will navigate to the bank’s website and enter your login details.
If you are accessing the internet without a VPN, your can reveal your login details to anyone observing your network, such as hackers, government officials, network administrators, and so on.
In contrast, a virtual private network establishes a tunnel through which your data packets pass, keeping them hidden from other entities. When you use a VPN, your data is encrypted, and no one can read it except the intended recipient.
Advantages of using a VPN connection
There are substantial advantages of using a VPN connection, such as:
Network security: Enhances network security by stopping people, software, and web browsers from gaining access to your connection.
Prevent data throttling: A virtual private network can help you avoid a data cap because no one, including your internet service provider, can see how much data you’re using.
Securing private information: A virtual private network provides high-level security features such as 256-bit encryption. This renders all of your online communications incomprehensible to anyone who is able to intercept them.
Scalability of a private network: The cost of expanding a private network can be prohibitively expensive. However, if you use a virtual private network server, you can provide access to multiple employees and remote workers at the same time.
Access to geo-blocked services: Some websites and services prohibit users from certain countries from accessing some or all of their content. In this case, you can use a virtual private network to appear to be using the internet from a location acceptable to the service you are attempting to access.
How to choose the right VPN?
Before you sign up for a VPN service, consider the following:
Provider’s logging policy: It will inform you what data a VPN provider will store regarding your web activity, so make sure you read it to protect your privacy. Always choose a vendor with a “no logging policy.”
Level of encryption: The strength of encryption is an essential factor to consider when selecting a VPN. More robust encryption is more difficult to crack and provides greater security. In the virtual private network industry, 256-bit encryption is standard.
Connection speed: One disadvantage of using a virtual private network is that it can slightly slow down your internet connection due to the additional encryption step the data goes through. To mitigate this slowdown, you’ll need a virtual private network with fast servers.
Available servers: Having more servers gives you more options for connecting to a fast and reliable server.
VPN provider’s country: You should avoid VPNs from the United Kingdom, the United States, Canada, Germany, Belgium, Italy, as well as Denmark, France, the Netherlands, Norway, Australia, New Zealand, Spain, and Sweden. Local security agencies in these countries may force a virtual private network provider to reveal the data of its users.
How to set up a VPN?
There are several methods for manually configuring a virtual private network on android, windows, Mac, and iOS:
Here are the steps for configuring a virtual private network on android:
- Navigate to the Settings > Wireless & Networks > More menu.
- Tap the plus (+) icon in the upper right corner.
- Enter the credentials you received from your service provider.
- To complete the process, click the Save button.
Here are the steps for configuring a virtual private network on windows:
- Navigate to Network Settings > VPN > Add a VPN Connection.
- Fill out the form with all of the necessary information.
- From the VPN Provider drop-down menu, select Windows (built-in).
- Choose PPTP from the VPN type drop-down menu.
- Choose the Remember my sign-in information option.
- Click Save, select the VPN, and finally click the Connect button.
Here are the steps for configuring a virtual private network on Mac:
- Select Network from the System Preferences menu on your Mac.
- Click plus (+) in the lower-left corner of the page to add the virtual private network connection.
- Enter the correct login information from your service provider and then click Apply.
- Click Connect after selecting the virtual private network connection from the list.
Here are the steps for configuring a virtual private network on iOS:
- Select VPN from the General section of the Settings app.
- Select Add VPN Configuration and Type as PPTP Protocol.
- Return to the previous screen and enter the information from your virtual private network providers, such as username, password, and server name.
- Click Done to begin using the virtual private network and then toggle the status switch.
You can also explore- What are the Different Types of Firewalls?
Conclusion
A virtual private network establishes a safe connection between you and the online world, improving your security. So, rather than being sorry later, use a VPN.
FAQs
What are the essential VPN features?
The following are some of the key features: VPN protocols Kill switch Leak protection Malware & ad blockers, etc.
How does a VPN function?
A VPN conceals your IP address by acting as a middleman and rerouting your traffic.
A VPN is a type of software?
VPN software is a piece of software that allows users to establish a secure, encrypted connection.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio