What is an Advanced Persistent Threat (APT)?
An Advanced Persistent Threat, or APT, is a sophisticated cyberattack. It stealthily breaches networks, often undetected for long periods. Unlike conventional threats, APTs focus on long-term access to targeted systems.
In this article, we will discuss all there is to know about APTs. But before diving deeper, let's go through the topics we will cover in this article.
Table of Content (TOC)
- What is an Advanced Persistent Threat (APT) in Cybersecurity?
- How Do Advanced Persistent Threats Differ from Regular Cyber Threats?
- Notable APT Incidents
- How do APT (Advanced Persistent Threat) Progress?
- What Are Uncommon Indicators of APT Intrusions?
- What Cybersecurity Measures Can Thwart APT Attacks?
- What Future Threats Do Advanced Persistent Threat Hacking Pose?
- Enhance Your Cybersecurity Skills with Free Courses on APTs
What is an Advanced Persistent Threat (APT)?
APT Definition: An Advanced Persistent Threat is an extensive, well-coordinated attack campaign. In this attack, intruders establish an unauthorized, long-term presence in a network to extract sensitive data from large organizations, financial sectors, legal services, consumer goods, industrial telecoms, and government networks and remain undetected.
Perpetrators often use remote file inclusion (RFI) attacks, SQL injection, and cross-site scripting (XSS) to establish a foothold in a targeted network. Once they have gained access, they use Trojans and backdoor shells to expand their foothold and create a persistent presence within the targeted perimeter.
The effects of APTs are serious. They can steal trade secrets, get private employee data, damage critical systems like databases, or even take over entire websites.
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
How Do Advanced Persistent Threats Differ from Regular Cyber Threats?
APTs are different from regular or traditional cyber attacks in many ways, such as:
- APTs are not hit-and-leave attacks; instead, the attacker stays in the network to gather as much information as possible.
- These attacks are carefully planned and not random.
- APTs are conducted manually and target the whole system instead of a specific part, as done in regular attacks.
- APTs require more effort and resources than regular web attacks.
- These attacks are done by cybercriminals with extensive knowledge (Black Hat Hacker) and strong financial backing.
- Governments often employ these attacks for cyber warfare.
Notable APT Incidents
Equifax
In 2017, Equifax suffered a major APT incident where hackers gained access to sensitive personal information of over 143 million customers, including names, social security numbers, birth dates, and addresses. The breach was caused by a vulnerability in Equifax's web application software, which the hackers exploited to access the company's network.
Ukrainian Power Grid
In 2015, the Ukrainian power grid was targeted by a group of hackers known as SandWorm, who used sophisticated malware to cause a power outage that affected over 200,000 people. The hackers gained access to the power grid's network by exploiting vulnerabilities in the grid's software and hardware.
Sony Pictures
In 2014, Sony Pictures was targeted by a group of hackers known as the Guardians of Peace, who gained access to Sony's network and stole sensitive data, including unreleased movies, employee information, and confidential emails. The hackers used a combination of social engineering and malware to gain access to Sony's network.
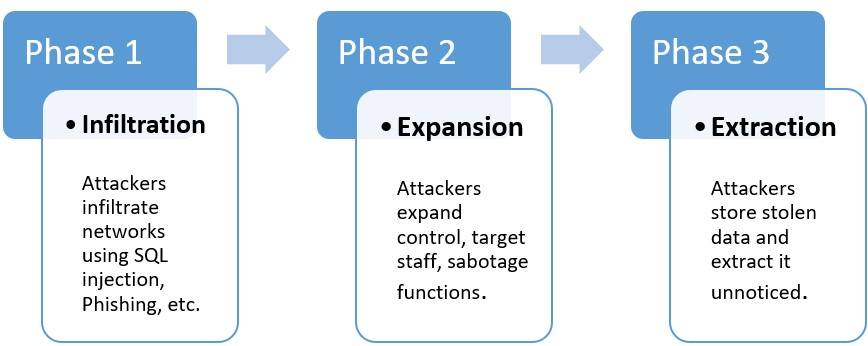
How do APT (Advanced Persistent Threat) Progress?
APT attacks happen in three stages: getting into the network (Infiltration), expanding their control (Expansion), and then stealing data (Extraction), all without getting caught.
Stage 1 – Infiltration
Attackers get into networks through web assets, network resources, or by tricking people. They use methods like SQL injection or spear phishing over email, using zero-day viruses, which are common threats to big organizations. Sometimes, they also launch DoS attacks to distract and weaken security, making it easier to get in. Once in, they install malware like backdoor shells or Trojans. This lets them control the network secretly.
Stage 2 – Expansion
Next, attackers spread their control inside the network. They target staff with access to essential data. This way, they get critical information like product details, employee data, and financial records. They can use this data differently, like selling it, changing it to harm the company's products, or taking down the whole organization. If they want to sabotage, they take control of important functions and use them to cause damage, like deleting databases and disrupting communications.
Stage 3 – Extraction
While the attack occurs, stolen data is stored safely inside the network. When they have enough, they move it out without getting caught. They might use distractions like another DDoS attack to keep the security team busy. This helps them take the data without being noticed.
What Are Uncommon Indicators of APT Intrusions?
Advanced Persistent Threat intrusions often manifest through subtle, easily overlooked signs. Understanding these indicators is crucial for early detection and response.
- Targeted Spear-Phishing Emails: Unlike general phishing attacks, spear-phishing in APTs involves highly personalized emails targeting specific individuals or roles within an organization, like executives or network administrators. These emails, often from unknown sources or with suspicious attachments, leverage detailed surveys about the targets.
- Unusual Logins: APT attackers may use compromised accounts to move through and escalate privileges within the network. Look out for logins at odd hours or from accounts that suddenly access applications or data sources they don't usually use. Such activities could indicate the presence of APTs active in the network.
- Widespread Backdoor Trojans: The discovery of trojans on network endpoints is a significant warning sign. These trojans are not just regular malware but tools for APT groups to maintain network access. When detected, it's essential to consider who installed them and whether similar trojans are present elsewhere in the network.
- Unusual Data Transmissions: APTs often focus on exfiltrating sensitive data. Watch for atypical data movements, like large batches of data being transferred to unfamiliar locations or devices or significant data transfers within the network that deviate from standard patterns.
- Data Clumped and Ready for Export: Check for large data aggregations in unusual places within the network. These could be ZIP files or encrypted files, especially in sizes or formats not typically used by the organization. Such anomalies suggest preparations for data exfiltration, indicative of APT activity.
What Cybersecurity Measures Can Thwart APT Attacks?
A multi-layered security approach is essential to effectively combat advanced persistent threats (APTs). Here are vital measures to consider:
- Secure Network Perimeter: Implement two-factor authentication, enforce strong passwords, and regularly patch systems. Monitoring network activity is crucial to detect any unusual patterns.
- Endpoint Hardening: Harden your endpoints, like personal computers and mobile devices, by requiring strong passwords and keeping systems regularly updated.
- Regular Software Updates: Ensure operating systems, applications, and tools are always up to date to protect against known security threats and vulnerabilities.
- Access Control: Restrict network and user access to necessary information and regularly review access permissions. Implementing a least privilege policy ensures users have access only to the data and resources needed for their roles.
- Advanced Endpoint Protection: Use endpoint protection solutions with advanced threat protection and automatic updates to safeguard against sophisticated threats.
- Encryption: Encrypt all sensitive information, even when stored in the cloud, to prevent unauthorized access.
- Regular Audits: Conduct regular system audits to identify any unusual activity or security gaps.
- Staff Training: Educate employees about APTs, their signs, and the correct response to suspicious activities.
- Malware Detection and Removal: Employ network traffic analysis, honeypots, host-based intrusion detection systems, and automated host-based analysis tools to detect and remove dormant and active malware.
- Firewalls and Access Control Systems: Use firewalls and authentication systems to block unauthorized access. Network segmentation controls communication between different network segments.
- Privileged User Management: Establish a tiered access control system with two-factor authentication. Regular audits of privileged user access are essential to ensure access is appropriately managed.
When combined and implemented effectively, these measures provide a robust defence against APT attacks, reducing the risk of infiltration and data breaches.
What Future Threats Do Advanced Persistent Threat Hacking Pose?
Advanced Persistent Threats (APTs) are evolving, posing new challenges to cybersecurity. Critical future threats include:
- Increased Use of AI in Spearphishing: APT actors are expected to leverage AI tools for creating persuasive spearphishing content. These AI-generated messages can mimic individual writing styles, making them more effective in tricking victims.
- Emergence of New Botnets and Rootkits: New botnets and rootkits, potentially more sophisticated, are likely to appear. These could obscure attacks, make attribution more complex, and mask attackers' infrastructure.
- Hacktivism Intertwined with APTs: Hacktivism is anticipated to be increasingly tied to APT activities, including DDoS attacks, disinformation campaigns, and destructive operations. This trend reflects the political motivations often driving APTs.
- Growth in Supply Chain Attacks: There could be an increase in supply chain attacks offered as a service on underground forums. This trend targets less secure small and medium-sized businesses as entry points to larger targets.
- Expansion of Hack-for-Hire Services: More APT groups may offer hack-for-hire services. This trend reflects a diversification of APT actors' activities and a potential increase in targeted attacks on behalf of third parties.
- Targeting of Smart Home Devices and MFT Systems: Smart home devices and Managed File Transfer (MFT) systems will likely be targeted more, exploiting their security weaknesses and integration into broader networks.
Enhance Your Cybersecurity Skills with Free Courses on APTs
If you want to learn more about APTs and how to mitigate them. In that case, you can explore our hand-picked free cybersecurity courses, such as "Advanced Cyber Security - Threats and Governance" and "Security Features and Advanced Threat Prevention." These courses are designed to deepen your understanding of APTs and enhance your ability to protect against such threats.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio



Comments
(1)
S
a year ago
Report
Reply to Susan Perez