What Is Clickjacking and How Does It Work?
Cyber attackers are constantly refining their techniques to avoid detection. Attackers employ a variety of tactics to achieve their objectives. Clickjacking is one such attack.
Clickjacking attacks use visual tricks to trick website visitors into clicking on user interface elements that perform actions on another website. So, precisely what is clickjacking? We will go over clickjacking in great detail in this article. But first, let’s go over the topics we’ll be covering in this blog:
- What is clickjacking?
- Working of a clickjacking attack
- Types of clickjacking attacks
- How to prevent a clickjacking attack?
- Conclusion
What is clickjacking?
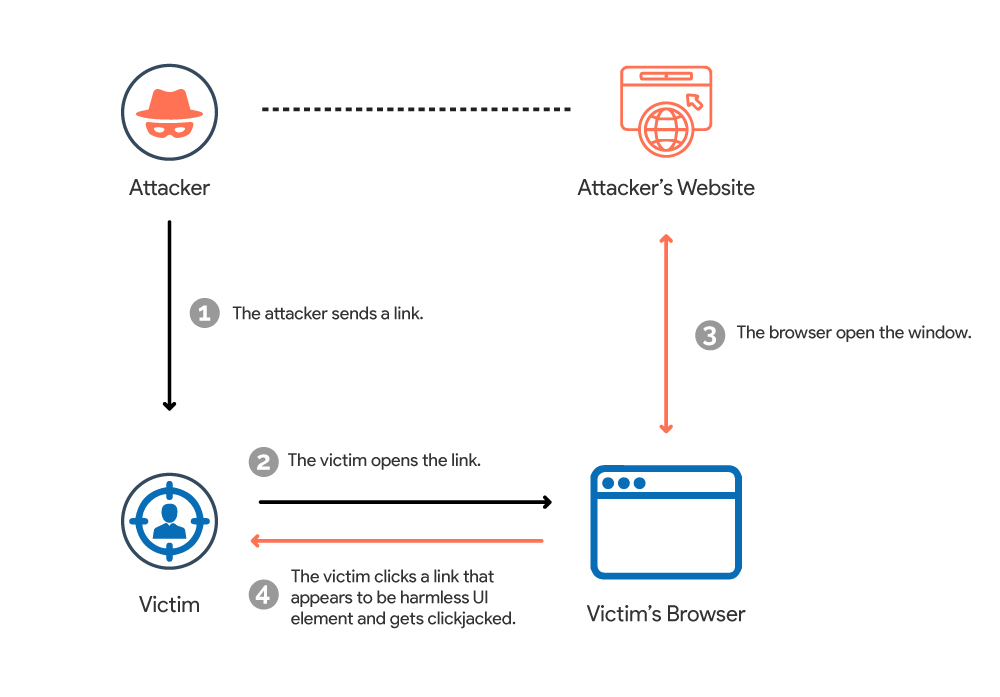
Clickjacking, also known as click hijacking, is a cyber attack that deceives people into clicking an invisible or disguised webpage element. Attackers accomplish clickjacking by showing a hidden page or HTML element within an iframe on top of the page the user is viewing. Since clickjacking takes place on a hidden iframe layer loaded on a genuine page, visitors are typically unaware of the attack.
You should also explore – What is cybersecurity?
Note: An iframe is a type of HTML element that loads another HTML page within the document.
Best-suited Cyber Security courses for you
Learn Cyber Security with these high-rated online courses
Working of a clickjacking attack
Attackers make clickjacking possible through HTML frames or iframes, which display web pages within other web pages via frames. Attackers can hide and transparently cover the initial web page with their user interface elements if a web page is depicted within a frame. The external appearance of the web page is still the same, giving users no reasonable grounds to suspect something is wrong.
Let’s look at an example of a clickjacking attack to see how it works:
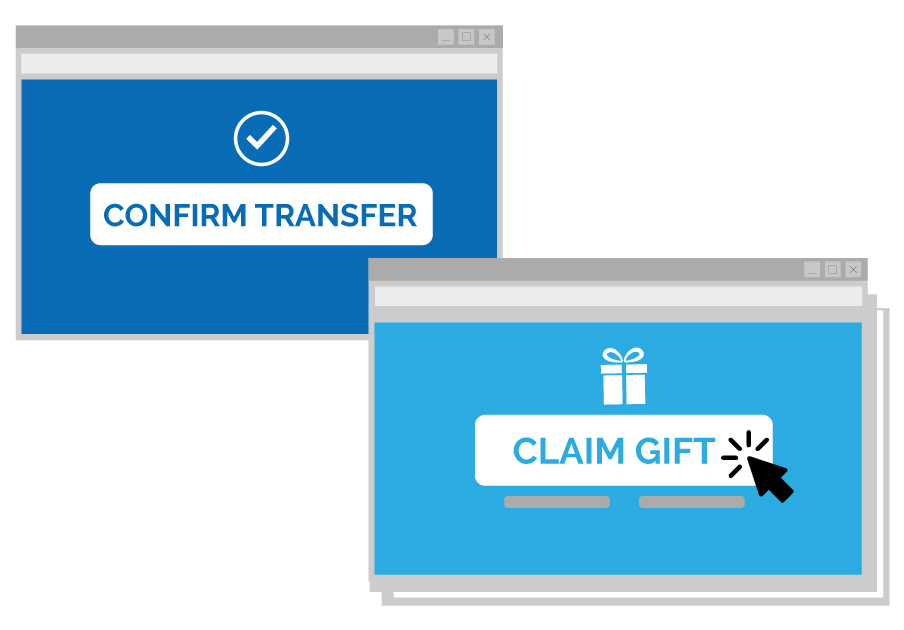
Assume an attacker creates an appealing page that promises users a free Amazon gift voucher worth $100. After seeing this, the victim thinks to claim the voucher. In the background, the attacker loads the screen that allows fund transfers. The bank transfer page is displayed in a hidden iframe just above the freebies page, with the “Confirm Transfer” button precisely aligned over the user-visible “Claim Gift ” button. When the user reaches the page, they click the “Claim Gift” button. In reality, the user has clicked the “Confirm Transfer” button after clicking on the invisible iframe. And thus becoming a victim of a clickjacking attack.
Types of clickjacking attacks
Here are various types of clickjacking attacks. Some of those attacks are:
Activation of the webcam and microphone: In this attack, a user’s Adobe Flash settings are loaded invisibly over another link. When users click the infected link, their Adobe Flash plug-in settings are altered, thus enabling their webcam and microphone.
Likejacking: When users click on a presented link, they are tricked into clicking a Facebook page “like” button and thus liking a page they didn’t intend to like.
Money transfer scams: In this attack, an attacker tricks you into clicking a link on a malicious website that authorizes the transfer of funds from your bank account.
Cursor-jacking: In this attack, an attacker creates and attaches a duplicate cursor to the actual cursor at a predetermined angle. The attackers, in this case, employ a technique that moves the cursor from the user’s perceived position to another.
Malware downloads: When a user clicks on a phished link, an attacker can start the download of malware. This allows for a variety of malicious actions, such as:
- Credential theft
- Making unauthorized purchases
- Determining your location
- Increasing clicks on unrelated websites
- Increasing ad revenue on websites, etc.
You can also explore – What is a phishing attack?
How to prevent a clickjacking attack?
The most effective method of defending against clickjacking attacks depends on where you are in the attack. Client-side defenses differ from server-side defenses, but both are critical.
Let’s first discuss how to prevent a clickjacking attack on the client-side:
There are mainly two ways in which you can prevent a clickjacking attack on the client-side:
Use a browser that is compatible with the Intersection Observer API.
The Intersection Observer API can monitor target elements’ “visibility” on a web page. The browser can use this API to detect when a framed window is being hidden. Various browsers support the API, including Google Chrome 58 and above, Mozilla Firefox 55 and above, Microsoft Edge 16 and above, Opera 45 and above, and others.
You should also explore – What is Adware & How do I Get rid of it?
Use a browser extension
Several browser add-ons can help protect you from clickjacking attacks. Some popular browser add-ons include NoScript and NoClickjack.
Now, let’s discuss how to prevent a clickjacking attack on the server-side:
There are mainly two ways in which you can prevent an attack on the server-side:
X-Frame-Options directive
An X-Frame-Options response header is part of a page’s HTTP response and signifies whether the browser has the approval to render a page within an iframe, frame, or object tags. Developers mainly developed it to protect against such attack.
In general, there are three options:
- DENY: No domain can display a page within an iframe.
- SAMEORIGIN: Only if the other page is in the same domain can the specified page be displayed in a frame on another webpage.
- ALLOW-FROM URI: Only a specific uniform resource identifier can display the specified page in a frame (URI).
Must explore – What is Spyware & How to Protect Yourself From It?
Policy on Content Security
CSP’s frame-ancestors directive can control content embedding by malicious pages using iframe, object, and so on. Modern browsers support CSPs. Thus it also allows site owners to control what content should load on a page. CSPs can prevent clickjacking and cross-site scripting attacks by defining server origins and script endpoints.
Conclusion
Clickjacking is a particularly nasty attack. Visitors and website administrators, thankfully, have a defense. So, it’s preferable to take the precautions discussed above than to be sorry later!!
FAQs
What can a clickjacking attacker do?
An attacker can use a clickjacking attack to trick users into unknowingly downloading malware, visiting malicious web pages, providing credentials or sensitive information, transferring money, or purchasing products online.
Clickjacking is classified as which type of risk?
Because of the potential risks posed by clickjacking and its inherent impact, it is classified as a moderate risk in most critical applications, such as banking or sensitive data handling apps.
What exactly is clickjacking in the context of cyber security?
Clickjacking is a cybersecurity attack that tricks users into thinking they are tapping on one thing while clicking on another.
Can CSP protect against clickjacking?
Yes, Content-Security-Policy can keep clickjacking at bay. It is an HTTP response header that includes a frame-ancestors directive to prevent clickjacking.
What is an iframe?
An iframe is a type of HTML element that loads another HTML page within the document.
This is a collection of insightful articles from domain experts in the fields of Cloud Computing, DevOps, AWS, Data Science, Machine Learning, AI, and Natural Language Processing. The range of topics caters to upski... Read Full Bio