What is a Masquerade Attack?
You receive an urgent email from your boss asking for confidential files. The email looks real—same name, same signature—but it’s a trap. Someone is pretending to be your boss to steal data. This is a Masquerade Attack—a cybercrime where attackers disguise themselves as trusted entities to gain unauthorized access.
Just like a thief wearing a uniform to sneak into a secure building, hackers use stolen credentials, fake identities, or malware to trick systems and people by using masquerade attacks. These attacks can compromise businesses, leak sensitive data, and cause financial losses.
Table of Content (TOC)
- What is a Masquerade Attack?
- Common Tools & Techniques Used in Masquerade Attacks
- How Does a Masquerade Attack Work?
- Types of Masquerade Attacks and Examples
- Real-World Examples of Masquerade Attacks
- What Are the Signs of a Masquerade Attack?
- How Can You Prevent a Masquerade Attack?
- Masquerade Attacks vs. Other Cyber Threats
What is a Masquerade Attack?
A Masquerade Attack is a type of active cyber attack that happens when an attacker impersonates a legitimate user or system to gain access to sensitive information.
Hackers may use stolen credentials, user identifiers, fake identities, or malicious software to trick security mechanisms and individuals and bypass authentication processes. These attacks can have severe consequences, including data breaches, financial loss, and security risks.
If you are intrested in knowing or learning about active attacks in cybersecurity, refer to the What is an Active Attacks article.
Common Tools & Techniques Used in Masquerade Attacks
Here are some of the common tools and techniques that attackers commonly use to perform masquerade attacks:
| Tool/Technique | Description | Example |
|---|---|---|
| Phishing Emails | Attackers send fake emails to steal login credentials. | An email posing as a bank requests login details. |
| Keyloggers | Malicious software records keystrokes to capture passwords. | A trojan installed on a computer logs keystrokes and sends them to hackers. |
| Session Hijacking | Hackers steal active session tokens to impersonate users. | An attacker intercepts a session and transfers money from a banking account. |
| MITM (Man-in-the-Middle) Attacks | Hackers intercept communication between two parties to manipulate or steal data. | A hacker sits between a user and a website, altering messages or login details. |
| Fake Websites (Spoofing) | Fraudulent websites mimic real ones to collect login details. | A fake PayPal website asks users to enter their credentials. |
| Credential Stuffing | Hackers use stolen usernames and passwords from past breaches. | Attackers try leaked passwords from one site on multiple platforms. |
| Malware & Trojans | Malicious programs secretly capture login details and send them to attackers. | A user unknowingly installs malware that steals and transmits credentials. |

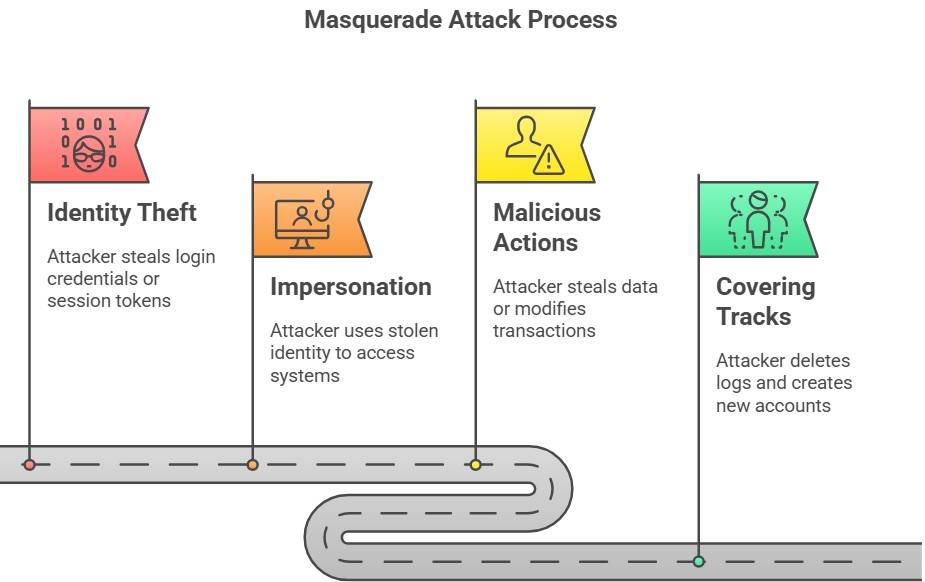
How Does a Masquerade Attack Work?
A masquerade attack happens when an attacker impersonates a legitimate user to gain unauthorized access. Here’s how it works:
Step 1: Identity Theft
The attacker steals login credentials, session tokens, or device details. They accomplish this by using phishing emails, keyloggers, credential stuffing, etc.
Step 2: Impersonation
The attacker uses the stolen identity to log into a system or network. They may use session hijacking to take over an active user session, spoof a trusted IP address to bypass security or access a system through compromised admin credentials.
Step 3: Malicious Actions
Once inside, the attacker can steal sensitive data like personal information, payment details, or intellectual property. They can also modify transactions in financial systems and even install malware or backdoors to maintain access and expand the attack.
Step 4: Covering Tracks
To avoid detection, the attacker deletes logs to erase traces of their activity, uses encryption to hide data transfers, or even creates new accounts with admin privileges to regain access later.
Types of Masquerade Attacks and Examples
| Attack Type | Description | Example |
|---|---|---|
| User Masquerade | An attacker steals valid user credentials (e.g., usernames and passwords) through phishing, social engineering, or brute-force attacks. They use these details to impersonate a real user and gain unauthorized access. | A hacker sends a phishing email posing as an IT department, tricking an employee into revealing their login credentials. |
| Device Masquerade | The attacker spoofs a trusted device’s identity (e.g., MAC or IP address) to exploit network trust relationships. | A hacker clones the MAC address of an authorized device to bypass network security and gain access to sensitive company data. |
| Website Masquerade | A fake website is designed to look like a legitimate one to deceive users into providing sensitive information like passwords or payment details. | A fraudulent banking website mimics the real one, tricking users into entering their login credentials. |
| Application Masquerade | A malicious application is disguised as a legitimate one, leading users to unknowingly install harmful software. Once installed, it can steal data or compromise the device. | A fake mobile banking app mimics an official app, harvesting users’ login information and sending it to attackers. |
| System Masquerade | The attacker manipulates or disguises a system as a trusted entity to intercept, redirect, or manipulate network traffic. | A rogue Wi-Fi hotspot is set up in a public space, appearing as a legitimate network, to steal login credentials from unsuspecting users. |
Real-World Examples of Masquerade Attacks
Here are some of the real word examples:
- Yahoo Data Breach (2013-2014): Hackers stole 3 billion user credentials and accessed private emails.
- Sony PlayStation Hack (2011): Attackers used stolen admin credentials to compromise 77 million accounts.
- Twitter Attack (2020): Hackers impersonated employees to gain control of high-profile accounts.
Understanding such attacks highlights the importance of cybersecurity in protecting personal and organizational data. If you are interested in a career in cybersecurity and want to know about top colleges, salary, etc., explore the What is Cyber Security content piece.
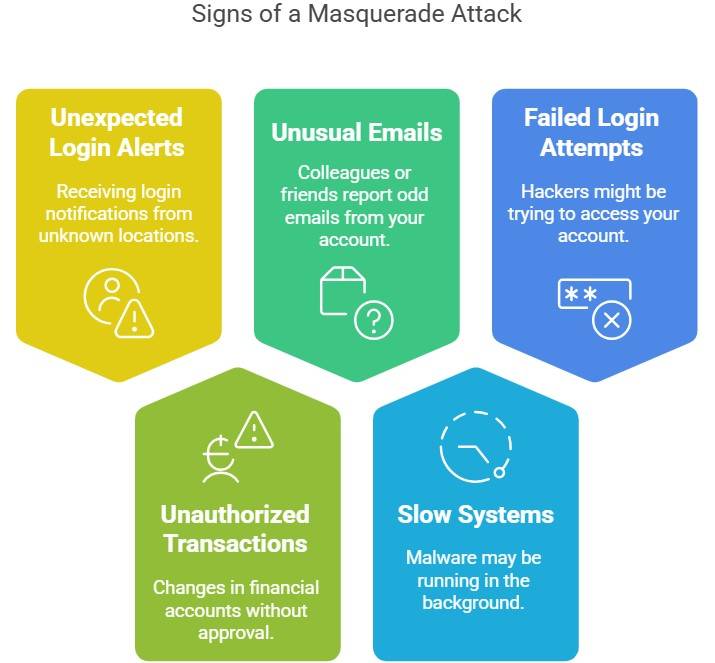
What Are the Signs of a Masquerade Attack?
Here are some of the signs that may be an indication of a masquerade attack:
- Unexpected Login Alerts: Receiving login notifications from unknown locations.
- Unauthorized Transactions: Changes in financial accounts without approval.
- Unusual Emails or Messages: Colleagues or friends report odd emails from your account.
- Slow or Unresponsive Systems: Malware may be running in the background.
- Multiple Failed Login Attempts: Hackers might be trying to access your account.
How Can You Prevent a Masquerade Attack?
Here are some of the practices that you must follow:
- Use Strong, Unique Passwords: Avoid using the same password for multiple accounts.
- Enable Multi-Factor Authentication (MFA): Adds an extra security layer.
- Regularly Update Software: Security patches fix vulnerabilities.
- Avoid Clicking Suspicious Links: Phishing emails can steal login credentials.
- Monitor Account Activity: Check for unauthorized logins or changes.
- Use Secure Networks: Avoid logging in from public Wi-Fi without a VPN.
Masquerade Attacks vs. Other Cyber Threats
Masquerade attacks are often confused with Replay Attacks and Spoofing Attacks. Here's how they differ:
Masquerade Attacks vs. Replay Attacks
| Aspect | Masquerade Attack | Replay Attack |
|---|---|---|
| Definition | Attacker impersonates a legitimate user | Attacker captures and replays valid data to trick a system |
| Method | Uses stolen credentials or fake identities | Resends intercepted login details or transactions |
| Goal | Unauthorized access, data theft | Fraudulent transactions or repeated access |
| Example | Hacker logs into an account with stolen credentials | Hacker records a bank transaction and replays it to steal money |
Masquerade Attacks vs. Spoofing Attacks
| Aspect | Masquerade Attack | Spoofing Attack |
|---|---|---|
| Definition | Attacker pretends to be a trusted user | Attacker fakes an IP, email, or website |
| Method | Uses real credentials or stolen data | Alters data to look legitimate |
| Goal | Gain unauthorized access | Trick users or systems into trusting fake data |
| Example | Hacker logs into a system using a stolen password | Fake website mimics a bank’s login page to steal credentials |
Conclusion
Masquerade attacks are a serious cybersecurity threat. Attackers disguise themselves as legitimate users to steal data, commit fraud, or disrupt operations. Recognizing warning signs, using strong authentication, pursuing cyber security courses & certifications online, and staying alert can prevent these attacks and keep data safe.
Must Explore Articles:





Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio