What Is Public Key Cryptography?
Millions of people rely on advanced technologies to store and exchange personal data. But, failure to protect data in travel can lead to significant failures and increased cybercrime. As a result, encryption has emerged as one of the most effective means of combating these issues. So, in this article, we will look at one of the most widely used and popular encryption schemes, public key cryptography.
So, what is public key cryptography, and how does it work? Before we answer these questions, let’s go through the topics we will cover in this article.
Table of contents (TOC)
- What is public key cryptography?
- How does public key cryptography works?
- Public key cryptography example
- Applications of public key cryptography
- Advantages of using public key cryptography
- Disadvantages of using public key cryptography
- Conclusion
You can also explore: What are Different Types of Cryptography?
What is public key cryptography?
Public key cryptography definition: Public key cryptography is a type of encryption technique that employs two keys that are mathematically related but not identical – one private or secret and one public.
In layman’s terms, it is a method of cryptography that requires two separate keys. One private for decrypting the data and one public for encrypting the data in order to protect it from unauthorized access or use.
Anyone can obtain the public key; it makes no difference who has and knows it. A public key is meaningless on its own, and its sole objective is to encrypt the data before it is returned to the holder of the private key, who can then decrypt it using only their private key. So, as long as the underlying cryptography is intact, you can be confident that no one but your friend is aware of your dirty little secret.
You can also explore: What are different types of cryptography?
The Rivest-Sharmir-Adleman (RSA) cryptography system is used for public key cryptography. This algorithm is commonly used when transmitting secure, sensitive information over an unprotected network like the internet. The RSA algorithm is widely regarded because it allows public and private keys to encrypt messages while maintaining their confidentiality and authenticity.
You can also explore: Types Of Computer Networks
Best-suited Networking courses for you
Learn Networking with these high-rated online courses
How does public key cryptography works?
The algorithm used to generate the key is publicly known, which is how both parties can create key pairs, but no one else can decrypt messages sent without the seed number used to generate the private key.
Each party, i.e., the receiver and sender, generates two keys – private and public keys. The public key can be given to anyone because its sole purpose is to encrypt the sent data. Anyone with access to the private key (recipient) can decrypt it. Anyone can steal the public key, but all they can do with it is encrypt the data. As a result, the data remains secure and is only accessible to the party possessing the private key.
As stated above, the RSA algorithm is widely used for this type of cryptography. Let’s dive deeper into this statement. The RSA algorithm is divided into four stages, which are as follows:
- Key generation (first stage): Create a private key to keep and a public key to share.
- Key distribution (second stage): Distribute the public key throughout the network.
- Encryption (3rd stage): The sender encrypts the message using the receiver’s public key.
- Decryption (4th stage): The receiver decrypts the message using its private key.
Note: If you want to know how to create keys or about the working of the RSA algorithm, you can refer to the Do You Know: What Is a RSA Algorithm article.
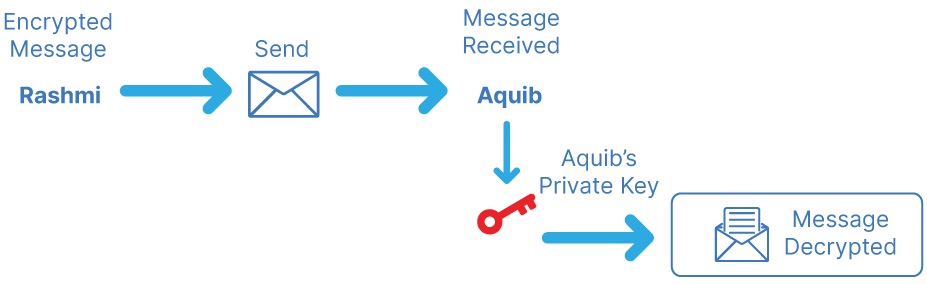
Public key cryptography example
An HR representative (Rashmi) from Naukri.com wishes to send Aquib an encrypted email. Rashmi encrypts the message using Aquib’s public key, and when Aquib receives it, he uses his private key to decrypt the message from Rashmi.
Although attackers may attempt to compromise the server in order to read the message, they will be unable to do so because they lack the private key required to decrypt the message. Because he is the only one with the private key, only Aquib will be able to decrypt the message. Aquib simply repeats the process when he wishes to respond, encrypting her message with Rasmi’s public key.
Applications of public key cryptography
There are various public key cryptography applications, and some of the most common ones are digital signatures and encryption.
Digital signatures: A digital signature confirms the signer’s identity and ensures that the documents transmitted are not forged or tampered with. Digital signatures function similarly to electronic “fingerprints.” Some of the benefits of using digital signatures are:
- Speed: First and foremost, signing documents digitally is not the same as signing them on paper in terms of time management and ease of use. The administrative burden can hamper the sale and, in some cases, force it to be terminated. Using electronic signatures in your business could save you money.
- User Experience: Improving the user experience is a second overlooked benefit. Opening a signing email request simplifies printing, signing, and scanning a document to return it.
- Security: Identification and authentication checks provide a high level of protection for document access and signing capabilities.
- Fewer errors: By automating the digital signature process, the financial consequences of human errors, such as signing errors or document loss, can be reduced.
For more information, you can also explore: What is a digital signature?
Encryption: Encryption is a method of concealing information by transforming it into what appears to be random data. Some of the benefits of using encryption are:
- Confidentiality: Because the content is encrypted using the sender’s public key, it can only be decrypted using the recipient’s private key, ensuring that only the receiving party can decrypt the content.
- Integrity: Even the slightest change to the original content will cause the decryption process to fail, ensuring the content’s integrity.
Advantages of using public key cryptography
There are various advantages of this type of cryptography, and some of those advantages are:
- Authentication: Because public key cryptography allows for digital signatures, message recipients can confirm that messages are truly coming from a specific sender.
- Convenience: This type of cryptography addresses the issue of distributing encryption keys by having everyone publish their public keys while keeping private keys private.
- Non-repudiation: Digitally signed messages function similarly to physically signed documents. It is essentially the same as admitting a message; thus, the sender cannot deny it.
- Tampering detection: Message recipients can detect tampering using digital signatures in public key encryption.
Disadvantages of using public key cryptography
As almost everything has its advantages and disadvantages, public key cryptography also has some disadvantages of its own, such as:
- Security: If an attacker discovers your private key, he or she can read all of your messages.
- Possibility of losing a private key: If your private key is lost, you will not be able to decrypt the received messages.
- Slow working: Because this method is slower than symmetric cryptography, it is unsuitable for decrypting bulk messages.
- Public keys are not authenticated: No one knows for certain that a public key belongs to the individual it specifies, so users must verify that their public keys truly belong to them.
Conclusion
The main advantage of this type of cryptography is its increased data security. Because users never need to transmit or reveal their private keys to anyone, public key cryptography remains the most secure protocol. Thus reducing the chance of cyber criminals discovering an individual’s secret key during transmission.
FAQs
What is public key cryptography?
Public key cryptography is a type of encryption technique that employs two keys that are mathematically related but not identical - one private or secret and one public.
What are the advantages of public key cryptography?
There are various advantages of public key cryptography, and some of those advantages are authentication, convenience, non-repudiation, tampering detection, etc.
What are the disadvantages of public key cryptography?
Some disadvantages of public key cryptography are low security, the possibility of losing a private key, slow working, unauthenticated public keys, etc.
What is another name for public key cryptography?
Public key cryptography is also known as public-key encryption and asymmetric encryption.
In accordance with public key cryptography, what is a public key?
In accordance with public key cryptography, a public key is a large numerical value used to encrypt data.
What is the biggest plus point of public key cryptography?
The biggest plus point of public key cryptography is its increased data security. Because users never need to transmit or reveal their private keys to anyone, public key cryptography remains the most secure protocol. Thus reducing the chance of cyber criminals discovering an individual's secret key during transmission.
Why is public key cryptography safe?
Public key cryptography is safe as it is based on complex mathematics; thus, it's not easy to guess the private key of any individual.
What is the cause of the slowness in public key cryptography?
Public key cryptography is slow because the keys are longer, and the server must calculate two different keys for encryption and decryption.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio