What is Smishing? How to Protect Against It?
If you ask 100 random strangers what smishing is, only a few will know what you’re talking about. However, once the term is defined, many people will realize they have firsthand knowledge of this attack.
- What is smishing?
- Real-life examples of smishing attacks
- Types of a smishing attack
- How does a smishing attack work?
- How to protect from smishing attacks?
- Conclusion
What is Smishing?
The majority of the world’s smartphones can receive a text message from just about any number in the world. Countless users are already aware of the risks associated with clicking a link in an email message. Fewer people know the risks of clicking links in text messages – a practice known as Smishing.
The term “smishing” refers to a type of phishing attack that specifically targets mobile devices. Instead of sending phishing content via email, smishers deliver their messages via SMS or MMS text messages. Victims are duped into providing the sensitive information to a disguised attacker in this variant of phishing. Malware or fraudulent websites can aid in smishing.
Best-suited Networking courses for you
Learn Networking with these high-rated online courses
Real-life examples of smishing attacks
- Tripwire reported a smishing campaign in September 2020 that used the United States Postal Service as a disguise. The threat actors sent text messages notifying receivers that they needed to click a link in order to view essential information about a future USPS delivery. The malicious link directed victims to a series of web pages designed to steal visitors’ Google account information.
- In 2020, CYFIRMA discovered a smishing campaign targeting Olympics fans in order to sell fake event tickets to steal personal and banking information.
- Verizon acknowledged a smishing campaign targeting users in 2022. The smishing text appears to be from the user’s phone number in the hope that the user will click on the malicious link within the message.
Another example of a smishing attack is- An attacker employs big brands with links ostensibly leading to the brand’s website. Typically, an attacker will inform the user that they have won millions or would provide a malicious link supposedly for locating packages.
Must Explore- What is Cybersecurity?
Types of a smishing attack
Smishing attacks can take many forms, but the following are the most common:
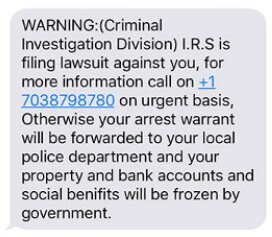
Urgent messages: An hacker will send text messages impersonating your bank or credit card company in order to get you to click a link or even provide classified info. They may inform you that your account has already been blocked and provide a link to solve this issue. They may also fabricate a fraudulent purchase and request that you confirm your authenticity to remove it.
COVID-19: These smishing scams are based on legitimate aid programs planned by government institutions, universal health care, or banking organizations to aid in COVID-19 recovery. Threat actors use these strategies to exploit victims’ financial and health concerns to commit fraud.
Financial services: These smishing attacks masquerade as alerts from banking firms. Nearly, everyone uses banking and credit card services, making them vulnerable. Signs of this attack can include loans and investing messages.
Survey links: In order to obtain the user’s confidential data, an attacker will send a fake survey link and ask the user to fill out the details. Fake survey links are more challenging to detect because most people do not want to take surveys, so even legitimate ones are usually unsolicited.
Order confirmation messages: In these attacks, an attacker uses a false confirmation of a recent purchase or billing invoice for a service. An attacker may send you a link to get you to take immediate action out of fear of being charged with something.
Brand messages: In order to portray themselves as helpful, more businesses are beginning to deliver messages for shopping or if there is unusual activity on their clients’ accounts. While this is beneficial in many ways, it allows attackers to blend in with this strategy.
Gift messages: These smishing attacks promise free services or products, usually from an authorized dealer. Limited-time offers, including an exclusive selection for a giveaway, can be signs of this attack.
Must Explore- Who is an Ethical Hacker?
How does a smishing attack work?
Cybercriminals using malware and malicious links carry out smishing attacks. Let’s look at an example to understand better how smishing attacks work:
An attacker sends you a text message that uses social engineering to trick you into thinking it is legitimate. You click on their infected link and give them your personal information, such as usernames, passwords, email addresses, etc. An attacker can then use this information to commit fraud or sell dark web data for quick cash.
An attacker can impersonate various organizations, including banks, healthcare providers, and courier services. And, to keep the user from thinking too long, they frequently inject a sense of urgency into the text messages.
How to protect from smishing attacks?
Attackers may use various techniques to deceive their targets, but several have comparable identifiers. Ensuring all staff knows the various types of smishing attacks can help them spot and stop them.
Here are a few more tips for detecting smishing and avoiding becoming a victim:
Don’t assume it’s genuine just because it’s professionally written: It’s a common misconception that scams have poor spelling and grammar. Although this is sometimes the case, many messages are meticulously crafted to look exactly real. Smishing makes this much easier because text messages are shorter than emails and don’t require any special formatting.
Never provide personal information via text: The most effective way to avoid scams is to never respond to an unsolicited email with personal information.
Confirm by going to the official website: I recommend you log in manually by typing the company’s address into your web browser. You should receive a notification with the same message if the message is genuine. And, if you do not see a notification, it is most likely a scam.
Avoid storing sensitive information on your phone: Most of us keep our banking information on our phones. Avoid keeping classified info on your mobile device. Because if an attacker installs malware on your smartphone, all of your sensitive data is at risk.
Using safe browsing: Google Safe Browsing is a free service that guards website owners and users against malicious websites and downloads. You can use this service to avoid falling victim to such an attack.
You can also explore – What is Safe Browsing & How to Turn It On?
Education: It is one of the most effective tools for assisting employees in avoiding smishing attacks. Ascertain that everyone on your team knows the various types of smishing attacks. This will aid them in detecting and stopping such attacks.
Conclusion
This article went into great detail about smishing, including topics like what it is? Its types? Examples? How to avoid it, and so on.
According to one report, smishing is among the quickest cyber threats, with up to 84 percent of organizations experiencing an attack last year. So, rather than being sorry later, I recommend you take the preventive measures discussed above!
FAQs
What could happen if you interact with smishing links?
When you are involved in a smishing attack, an attacker may ask you to visit a specific website. When you visit that website, malware may infiltrate your device and compromise your system and the data stored on it.
In a smishing attack, what type of device is targeted?
In a smishing attack, mobile phones are used as an attack platform.
What is the best way to avoid smishing?
The best way to avoid smishing is to avoid clicking on links in unfamiliar or unexpected text messages.
What makes smishing attacks so effective?
Text messagingu00a0feelsu00a0more casual and private than emails, thusu00a0making it easier to fall into the scammer's trick without feeling dubious.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio