What is Spyware?
More than 90% of computers worldwide are infected with spyware unknown to their owners. It’s one of the Internet’s oldest and most common threats, secretly infecting your computer to launch criminal activities such as identity theft or data breach. So, what is spyware? A spyware is a kind of malicious software installed on a computer but without the user’s knowledge.
In this article, we will go through spyware in great detail. But, before moving further, let’s see the topics listed under the table of content (TOC) that we will be cover in this blog:
Table of contenets (TOC)
- What is spyware?
- Types of spyware
- How does spyware work?
- What steps can you take to protect yourself from spyware?
- What are the signs of a spyware infection?
- How do you remove spyware?
Must Explore- What is Cybersecurity?
What is spyware?
Spyware is malicious software installed on your computer that begins tracking your online activity without your knowledge or permission. It accumulates information about an individual or organization in secret and relays it to third parties. Attacker installs it without the user’s knowledge through methods such as a trojan bundled with a legitimate program or a misleading pop-up window.
Spyware examples:
- CoolWebSearch: It exploits security flaws in Internet Explorer to gain control, change settings, and send browsing data to attackers.
- Emotet: It was one of the most common threats in the 2010s. It functioned as a Trojan, stealing banking credentials from its victims.
- Zlob: This program installs itself on a computer in order to record keystrokes and search a user’s browsing history.
- TIBS Dialer: In this case, a hijacker disconnects the victim’s computer from a local phone line and connects them to a toll number used to access pornographic websites.
Must Explore- What is a Denial-of-Service (DoS) Attack?
Best-suited Ethical Hacking courses for you
Learn Ethical Hacking with these high-rated online courses
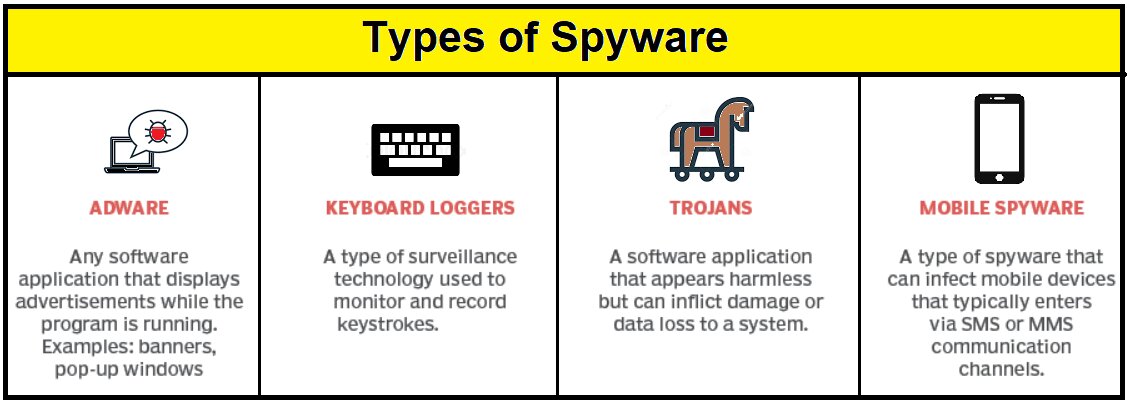
Types of spyware
It is generally of four types: adware, keyboard loggers, trojans, and mobile spyware.
Adware
Adware is malicious software that shows advertisements on your computer screen, most commonly within a web browser. It hides as a legitimate program or piggybacks on another program to trick you into installing it on your PC, tablet, or mobile device.
Keyboard loggers
Keyloggers record all that you type on a computer or mobile keyboard. These monitor your computer activity quietly while you use your devices normally. You can also use keyloggers for legitimate purposes, such as providing feedback for software development, but criminals use this to steal your data.
For more information, you can also explore: What Are Keystroke Loggers & How Do They Work?
Trojans
Trojans are malicious programs that appear to do one thing but do something else. Attackers can disguise trojans as free software, videos, or music, or they can appear as legitimate advertisements.
Mobile spyware
Mobile spyware monitors and records information about your actions without your knowledge or permission. It is dangerous because attackers can transmit it via text messages via short message services or multimedia messaging services and does not typically require user interaction to execute commands.
How does spyware work?
Spyware can infiltrate a device without the end user’s knowledge using an app install package, a file attachment, or a malicious website. It exists in its most benign form as an application that runs in the background as soon as the device is turned on. Its presence will consume random access memory and processor power and generate an infinite number of pop-up ads, effectively slowing down the web browser until it becomes unusable.
At its most dangerous, it will track web browsing history, passwords, and other private information such as email addresses, credit card numbers, personal identification numbers, or banking records. This data can be gathered and used for identity theft, or attackers can sell it to third parties. Attackers obtain the data by using keyloggers and screen captures.
Must Explore- What is a Phishing attack?
What steps can you take to protect yourself from spyware?
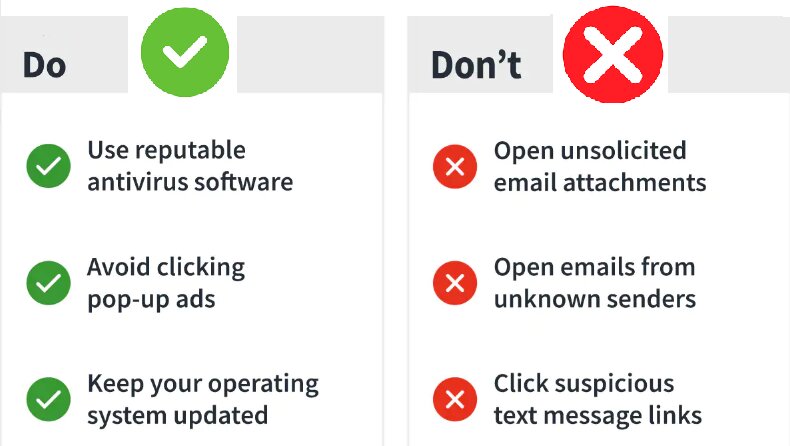
Some of the steps that you can take to protect yourself are:
- Make use of an antispyware scanner
- Pop-ups should be avoided at all costs
- Always read the terms and conditions
- Change your browser’s security settings
- Using only reputable antivirus software
- Setting up two-factor authentication
- Keeping up with browser, operating system (OS), and application software updates and patches
Let’s have a look at Do and Don’t:
What are the signs of a spyware infection?
Spyware can be difficult to detect on your device because it is designed to be deceptive and difficult to detect. Nonetheless, there are indicators that can help you determine whether you’ve been infected. If your computer exhibits the following symptoms, you may have a spyware problem:
- Your device is running slowly, unexpectedly crashing, or displaying error messages.
- Your device’s hard drive is nearly full.
- You’re annoyed by pop-ups that appear frequently and persistently.
- Your browser takes you to pages you haven’t visited before.
- Your browser is no longer directing you to your usual homepage.
- You discover icons for programs that you did not install on your device.
- Your browser has detected a new toolbar or plugin that you did not install.
How do you remove spyware?
Some of the ways to remove them are:
- Remove the internet connection.
- Remove the unwanted software from the device, and then reboot the entire system.
- Scan the system with reputable antivirus software. When the scan finds suspicious programs, it should prompt the user to clean, quarantine, or delete the software.
- Make use of a virus removal program.
- Allow an antispyware tool to run through the system.
If none of the preceding steps work, the user must access the device’s HD in safe mode. This, however, necessitates the use of a tool that allows the user to access the spyware folders and manually delete them. While this may appear to be a complicated process, it should only take a few minutes.

Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio


Comments
(10)
C
6 months ago
Report Abuse
Reply to Crista mia
C
6 months ago
Report Abuse
Reply to Crista mia
C
6 months ago
Report Abuse
Reply to Crista mia
J
7 months ago
Report Abuse
Reply to Jeffrey Bennet
N
7 months ago
Report Abuse
Reply to Natalie Paloma