What is Pretexting?
You receive a call from someone claiming to be your bank's representative. They sound professional and already know your basic details. They inform you about an issue with your account and ask for verification. Without thinking much, you share sensitive information. Later, you notice unauthorized transactions. You have just fallen victim to a Pretexting Attack.
Pretexting is a type of social engineering where attackers create a fake scenario (a "pretext") to trick you into revealing confidential information. Attackers may impersonate coworkers, IT staff, or even government officials to gain your trust.
Table of Content (TOC)
- What is Pretexting?
- How Does Pretexting Attack Work?
- Types of Pretexting Attack Techniques
- Real-World Examples of Pretexting Attack
- Pretexting vs Phishing Attack
- Impact of Pretexting on Businesses and Individual
- How to Detect and Respond to Pretexting?
- How to Prevent Pretexting Attack?
What is Pretexting?
Pretexting is a social engineering attack where an attacker creates a fake story to trick the victim into sharing private information. Instead of hacking systems, they manipulate human trust to get details like passwords, bank information, or security codes.
Attackers make their stories believable by using official logos, formal language, and professional messages. They may pretend to be a government official, IT support, or a bank representative. Their goal is to make the victim feel pressured or obligated to share information.
Pretexting can happen online, in person, or over the phone. The attacker collects details that help them plan a bigger attack later, such as identity theft or financial fraud. A pretexting attack is quite dangerous, as it can also bypass security protections like DMARC, which prevents fake emails.

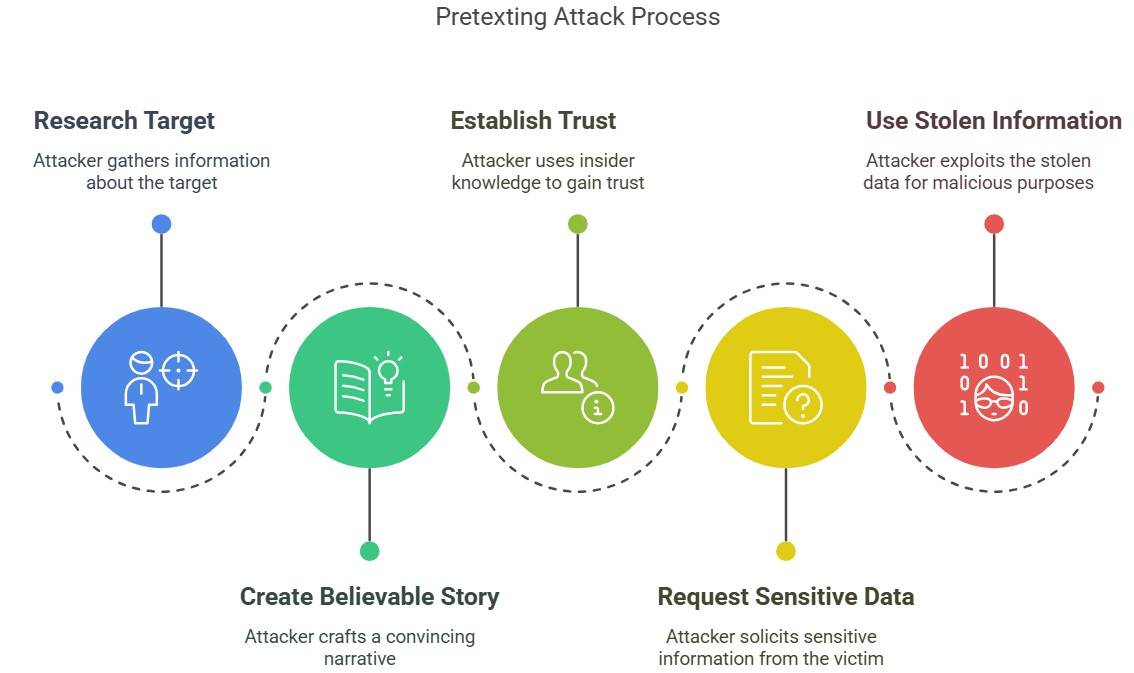
How Does Pretexting Attack Work?
A pretexting attack follows a structured approach. The attacker:
- First, researches about the target. They (attackers) gather details from social media, data breaches, or public records.
- Once the data has been gathered, they create a believable story by impersonating a trusted person or authority, such as a bank employee, police officer, or IT support.
- The attacker then uses insider knowledge to establish trust and appear legitimate.
- Once the victim falls for it, they ask for sensitive data like passwords, account numbers, or personal details.
- Once the attacker has the requested information, they use it for fraud, identity theft, unauthorized access, and other malicious activities.
Types of Pretexting Attack Techniques
Here are some of the most common types of pretexting attack techniques that are commonly employed by attackers:
| Type | Description |
|---|---|
| Impersonation | Attackers pose as bank officials, government agents, or IT staff to trick victims into sharing sensitive information. They may use personal details to appear more convincing. |
| Tailgating | An attacker follows an authorized person into a restricted area, pretending to have lost their ID or acting as a delivery person. |
| Piggybacking | Similar to tailgating, but with permission. Attackers exploit kindness by asking someone to hold the door open for them to gain unauthorized access. |
| Baiting | Attackers leave infected USB drives or links in places where victims are likely to pick them up and use them, leading to malware infections or data breaches. |
| Phishing | Attackers send fraudulent emails or messages that appear legitimate, tricking victims into clicking malicious links or sharing sensitive data. |
| Vishing | Attackers call victims, pretending to be from banks, government agencies, or IT support, to extract information. |
| Smishing | Attackers send fraudulent text messages with fake links, claiming urgent action is needed. |
| Scareware | Victims receive fake security alerts claiming their device is infected. They are urged to download malicious software or enter personal details on fraudulent websites |
Do you know how phishing and vishing attacks differ? If not, read the Difference Between Phishing and Vishing article.
Real-World Examples of Pretexting Attack
Here are some real-life cases that highlight the actual dangers of pretexting and how it can impact individuals and organizations alike.
- The Indian Digital Arrest Scam: Scammers impersonate police officers and tell victims they are under a - digital arrest. They claim that a package in the victim's name contains illegal substances and demand money to clear the charges. Many people have fallen victim to this well-planned deception.
- The Twitter Bitcoin Scam (2020): Hackers used pretexting to trick Twitter employees into resetting credentials. They then hijacked high-profile accounts, including Elon Musk and Barack Obama, to promote a Bitcoin scam.
- Facebook & Google Invoice Scam (2013-2015): A scammer impersonated a vendor and tricked employees at Google and Facebook into making fake payments amounting to $100 million.
To understand cybersecurity in depth, including certifications, course fees, syllabus, top colleges, and career opportunities, check out our detailed guide on Cyber Security: Certifications, Course Fees, Syllabus, Top Colleges, Salary, etc.
Pretexting vs Phishing Attack
For a better understanding, let's explore the difference between pretexting and phishing in a tabular format:
| Benchmark | Pretexting | Phishing |
|---|---|---|
| Approach | Creates a fake scenario to manipulate the victim. | Sends mass emails or messages with malicious links. |
| Targeting | Highly targeted and customized. | Often random and sent to many users. |
| Medium Used | Phone calls, in-person, or emails. | Emails, fake websites, SMS. |
| Example | A scammer posing as your HR department calls and asks for personal details. | An email with a fake login page asking you to enter your credentials. |
In layperson's terms, the main difference between pretexting and phishing is that phishing relies on email or fake websites. Meanwhile, pretexting is more personal and based on direct human interaction.
Impact of Pretexting on Businesses and Individual
Here are some of the impacts of a pretexting attack on businesses and individuals:
| For Businesses | For Individuals |
|---|---|
| Data Breach (Confidential information leak) |
Identity Theft (Stolen personal data can be used for fraud and other malicious activities) |
| Financial Fraud (Unauthorized money transfers) |
Financial Loss (Unauthorized transactions and drained accounts) |
| Reputation Damage (Loss of customer trust) | Emotional Distress (Victims feel violated and betrayed.) |
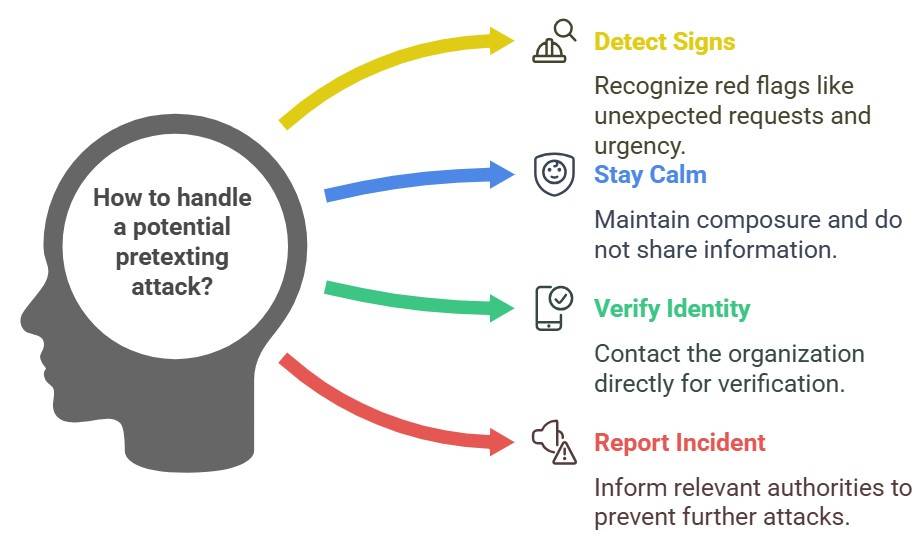
How to Detect and Respond to Pretexting?
How to Detect?
Here are some of the signs that may indicate you are being attacked using a pretexting attack:
- If someone asks for sensitive information unexpectedly or makes an unusual request - be cautious.
- The attacker may pose urgency and pressure to push you to make quick decisions. Take your time and think thoroughly.
- If you are able to find mismatched details, spelling errors, unknown email addresses, or strange phone numbers, then be cautious; these are all red flags.
- If you ask for official verification and they hesitate, it's a scam.
How to Respond?
Here are some of the practices that may help you from falling for these deceptive attacks:
- Stay calm, and do not share any information.
- Call the official organization directly to verify the caller's identity directly.
- Report the incident. Inform your bank, employer, or cybercrime cell about the incident.
- Educate others as awareness reduces future risks.
How to Prevent Pretexting Attack?
Here are some of the practices that you must follow:
- Never share sensitive information over calls or emails. Legitimate organizations never ask for passwords or OTPs over the phone.
- If someone claims to be an official, verify their credentials through official contact channels.
- Use Multi-Factor Authentication (MFA) as it adds another layer of security. Even if attackers steal your password, they won't be able to access the information due to MFA.
- If you suspect an attack, report it to your bank, IT team, or cybercrime authorities.
Conclusion
Pretexting attacks are dangerous as they rely on psychological manipulation rather than technical hacking. As a result, these attacks can even bypass security protections like DMARC, which is designed to prevent fake/fraudulent emails. So, to safeguard yourself and your organization from such deceptive attacks, it's essential to stay vigilant, verify identities, and report any suspicious activities.
Must Explore Articles:





Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio