What is Zero Trust Architecture and Its Benefits?
Zero Trust Architecture (ZTA) is a cybersecurity design that incorporates zero trust principles like strict access management, device and user authentication, and strong segmentation. It addresses the challenges of cloud computing, remote work, and evolving cyber threats that have expanded the attack surface.
Zero Trust Network Access (ZTNA) is a specific use case of ZTA that enables secure access to applications and data, even when they are outside the traditional security perimeter. By combining Zero Trust Architecture and ZTNA, organizations can create a secure foundation that allows their systems, services, APIs, data, and processes to be accessed from anywhere, anytime, and from any device.
Table of Contents (TOC)
- What is Zero Trust Architecture?
- What is the Need for ZTA?
- What are the Key Principles of a Zero Trust Architecture?
- How Does Zero Trust Architecture Work?
- What are the Benefits of Zero Trust Architecture?
What is Zero Trust Architecture?
Zero Trust architecture is a cybersecurity model that assumes no user or device should be trusted by default, regardless of whether they are inside or outside the network perimeter. It's important because traditional security models that rely on firewalls and VPNs are no longer sufficient in today's cloud and mobile environments.
Must Explore: What Are the Three Principles of Zero Trust?
Best-suited Networking courses for you
Learn Networking with these high-rated online courses
What is the Need for ZTA?
The need for Zero Trust architecture arises due to several key factors:
- Cyber Threats: Traditional perimeter-based security models are ineffective against modern threats like malware, credential theft, insider threats, and advanced persistent attacks that can bypass the perimeter.
- Dissolution of Perimeters: With remote workforces, cloud adoption, and increased mobility, a controlled corporate network perimeter no longer exists. Assets reside outside traditional boundaries.
- Expanded Attack Surface: Trends like BYOD, IoT, microservices, and APIs have significantly expanded the potential attack surface and entry points for threats.
- Data Breach Incidents: High-profile breaches have exposed that trusted insiders and compromised credentials can lead to massive data loss. (Capital One (2019) case, in which a former bank employee was accused of stealing the personal information of over 100 million customers and applicants.)
- Compliance Requirements: Regulations like GDPR, HIPAA, and PCI-DSS mandate tighter access controls, monitoring, and data protection aligned with zero trust principles.
- Need for Least Privilege: There is a need to strictly enforce least privileged access based on continuous verification of user, device, location, and other contextual factors.
What are the Key Principles of a Zero Trust Architecture?
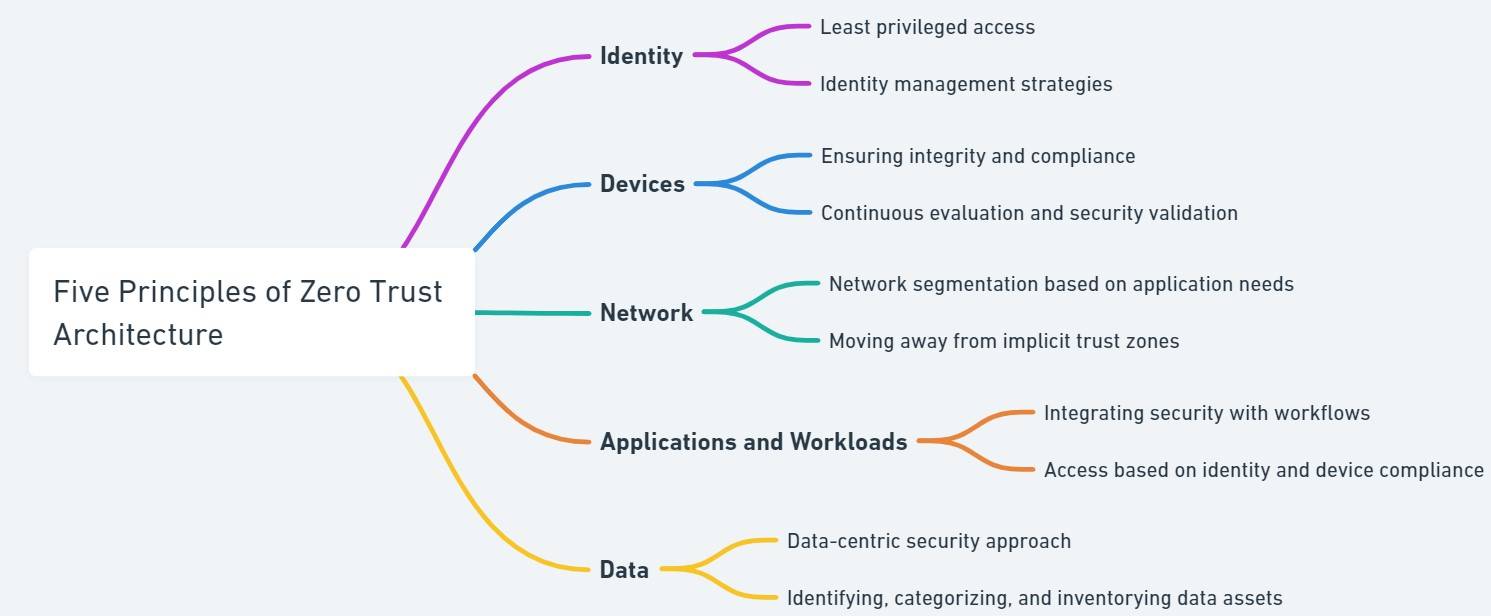
The US Cybersecurity and Infrastructure Security Agency (CISA) has laid out five key pillars for implementing Zero Trust: identity, devices, networks, applications and workloads, and data.
- Identity: Adopting the least privileged access approach to identify management.
- Devices: Ensuring integrity and compliance of devices accessing resources.
- Network: Aligning network segmentation and protections as per application/workflow needs rather than implicit trust zones.
- Application & Workload: Integrating security with application workflows, granting access to applications based on factors like - identity, device compliance, etc.
- Data: Adopting a data-centric approach, starting with identifying, categorizing, and inventorying data assets.
How Does Zero Trust Architecture Work?
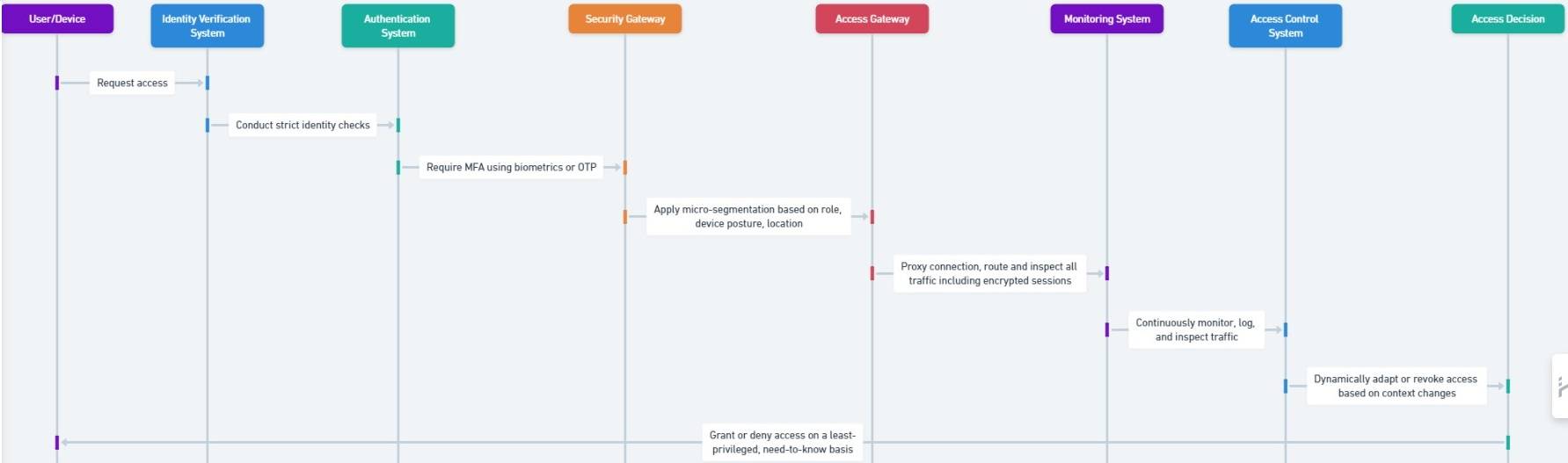
Here's how a Zero Trust Architecture typically works:
- By default, all users and devices are untrusted, whether they are inside or outside the corporate network perimeter.
- Before proceeding, the user and device must undergo strict identity verification and validation checks. For every application or resource access attempt, the user and device must be granted the least privileged access.
- Multi-factor authentication (MFA) is enforced, so all users must verify their identity using biometrics, one-time passwords, etc.
- Once authenticated, micro-segmentation and granular access controls are applied based on the user's role, device posture, location, and other contexts.
- All traffic is routed through a secure access gateway, which proxies the connection and inspects all traffic, including encrypted sessions, before allowing access.
- All traffic is continuously monitored, logged, and inspected to detect and respond to anomalies or threats in real-time.
- Access privileges are dynamically adapted or revoked if contexts change, such as a device becoming non-compliant or a user changing location.
- Access is provisioned on a need-to-know, least-privileged basis, limiting lateral movement within the environment.
There is no implicit trust in any user, app, device, or network—everything requires authorization and validation. The core idea is to create a perimeter around individual users and devices instead of networks, using identity as the control plane.
What are the Benefits of Zero Trust Architecture?
Here are some benefits of Zero Trust Architecture:
- Improved security posture: ZTA reduces the attack surface by limiting access to sensitive data and applications. It also ensures that all access attempts are verified and authenticated, reducing the risk of unauthorized access.
- Better visibility: It provides granular visibility into network traffic, allowing security teams to monitor and detect suspicious activity in real-time. This helps them identify and respond to security threats quickly.
- Enhanced compliance: It helps organizations comply with regulatory requirements by ensuring all data access is authenticated and authorized.
- Simplified access management: ZTA streamlines access management by eliminating the need for VPNs and other complex access controls. It also simplifies the user experience and reduces the risk of misconfiguration and human error.
- Increased resilience: It improves network resilience by implementing a "never trust, always verify" approach to security. It means that even if one part of the network is compromised, attackers will still need to pass multiple layers of security to gain access to sensitive data.
Must Read Articles:






Anshuman Singh is an accomplished content writer with over three years of experience specializing in cybersecurity, cloud computing, networking, and software testing. Known for his clear, concise, and informative wr... Read Full Bio